Information
Challenge Link: https://cyberdefenders.org/blueteam-ctf-challenges/packetdetective
Category: Threat Hunting
Level: Easy
Scenario: As a SOC analyst, explore a collection of Wireshark pcap files that delve into various attack tactics, including evasion and lateral movement. Analyze network traffic captured within these pcaps to uncover valuable insights and detect potential command and control (C&C) activities.
Supportive Tools
Walkthrough
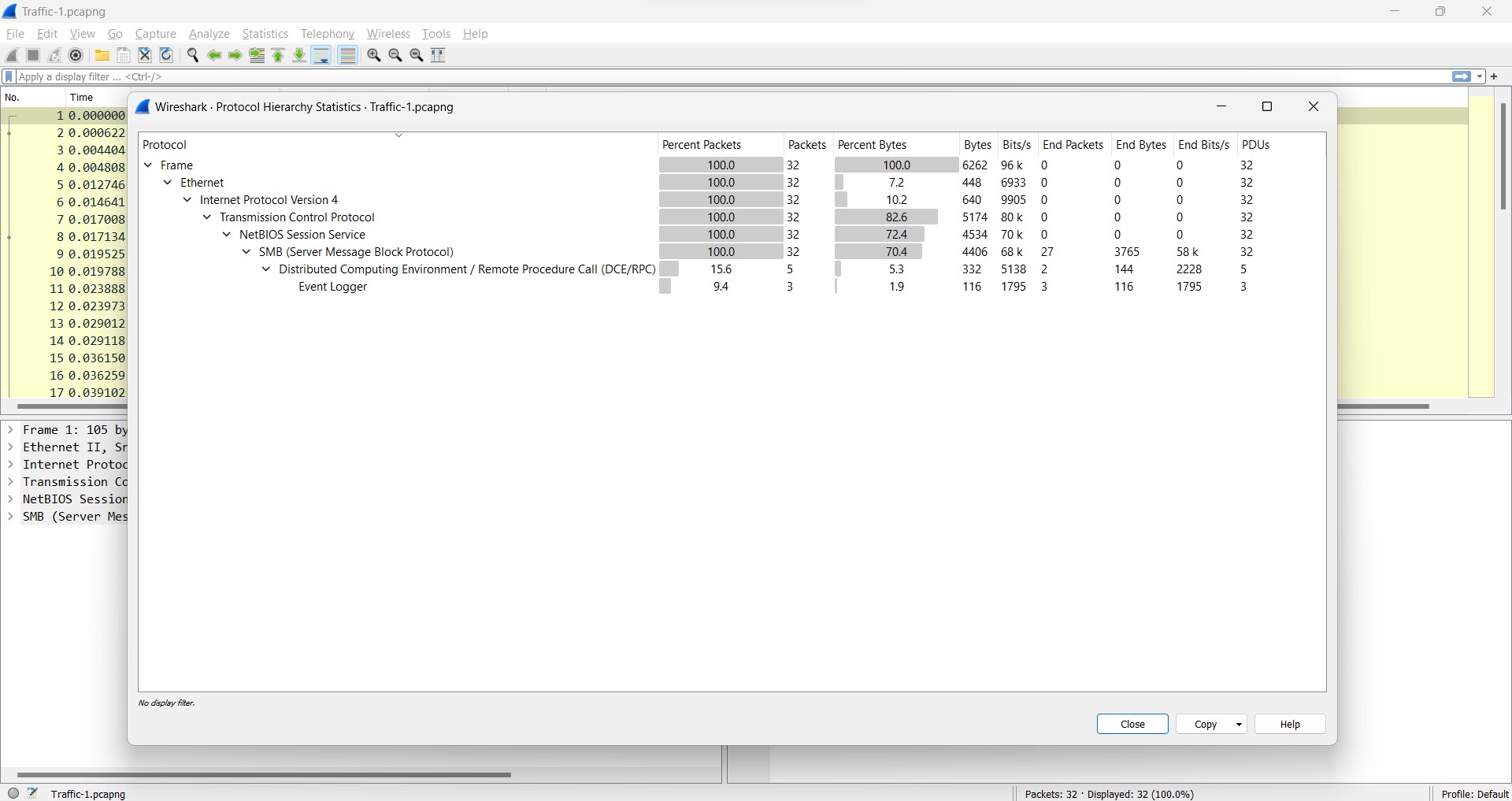
Q1) (File => Traffic-1) What is the amount of bandwidth being used by the SMB protocol in bytes?
The question is straight-forward. You can find the answer by going to Statistics > Protocol Hierarchy and you would find the answer rightaway.
Answer: 4***
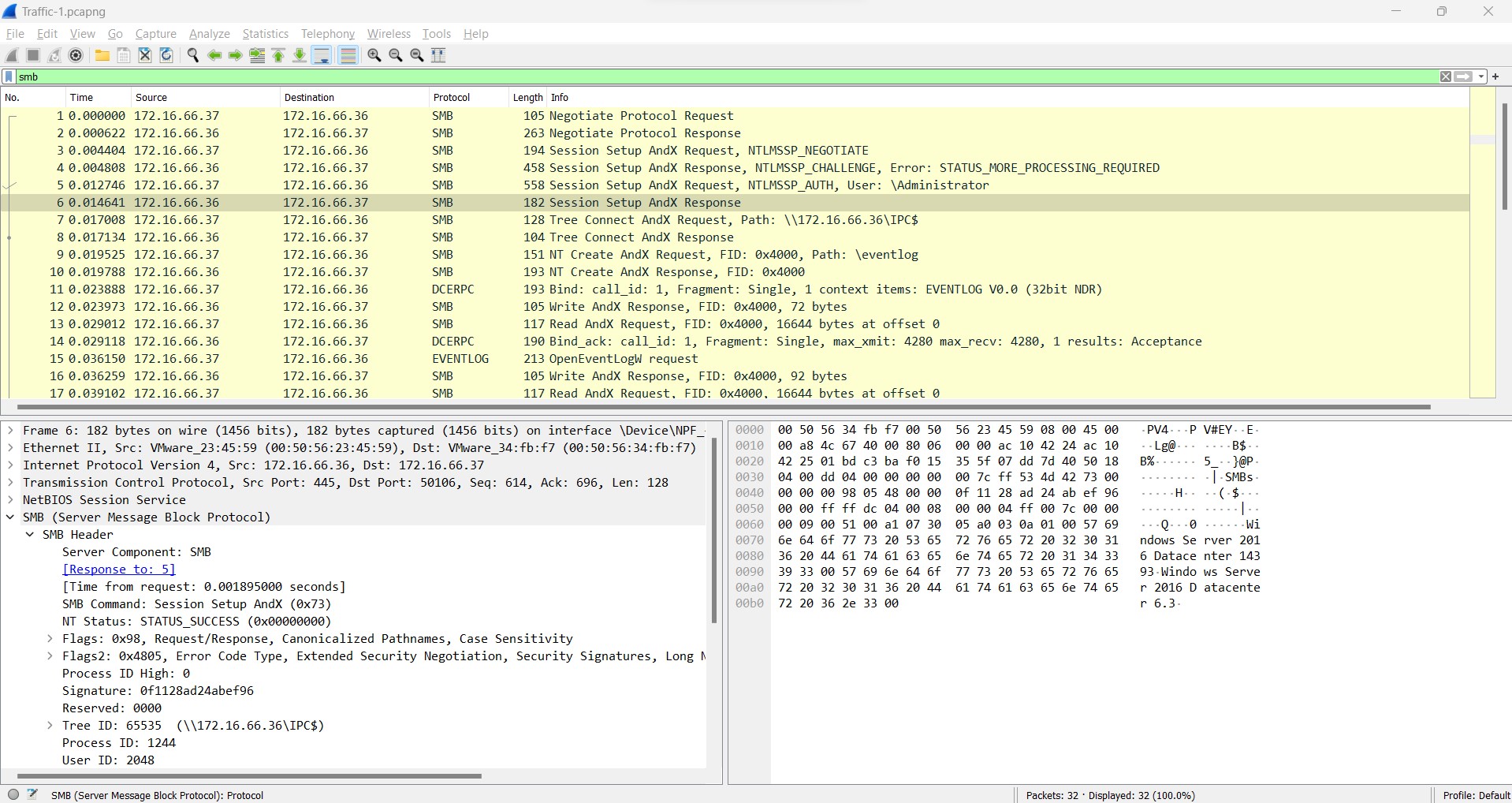
Q2) (File => Traffic-1) Which username was utilized for authentication via SMB?
To hunt for the username which was utilized for authenticating to the SMB service, there are several ways to achieve this. For me, I take a look at the info column which provides details about each packet, but before we are going to investigate each packet, make sure to filter just only the interested ones. In this case, SMB protocol. To filter it, just click on filter box below the main toolbar and search for smb.
After filter the packet protocol, you would see a lot of the information appears there which communicated using SMB protocol. By looking at the info column, you would directly see an interested username which used by malicious actor to authenticate to the SMB service.
Answer: A***********r
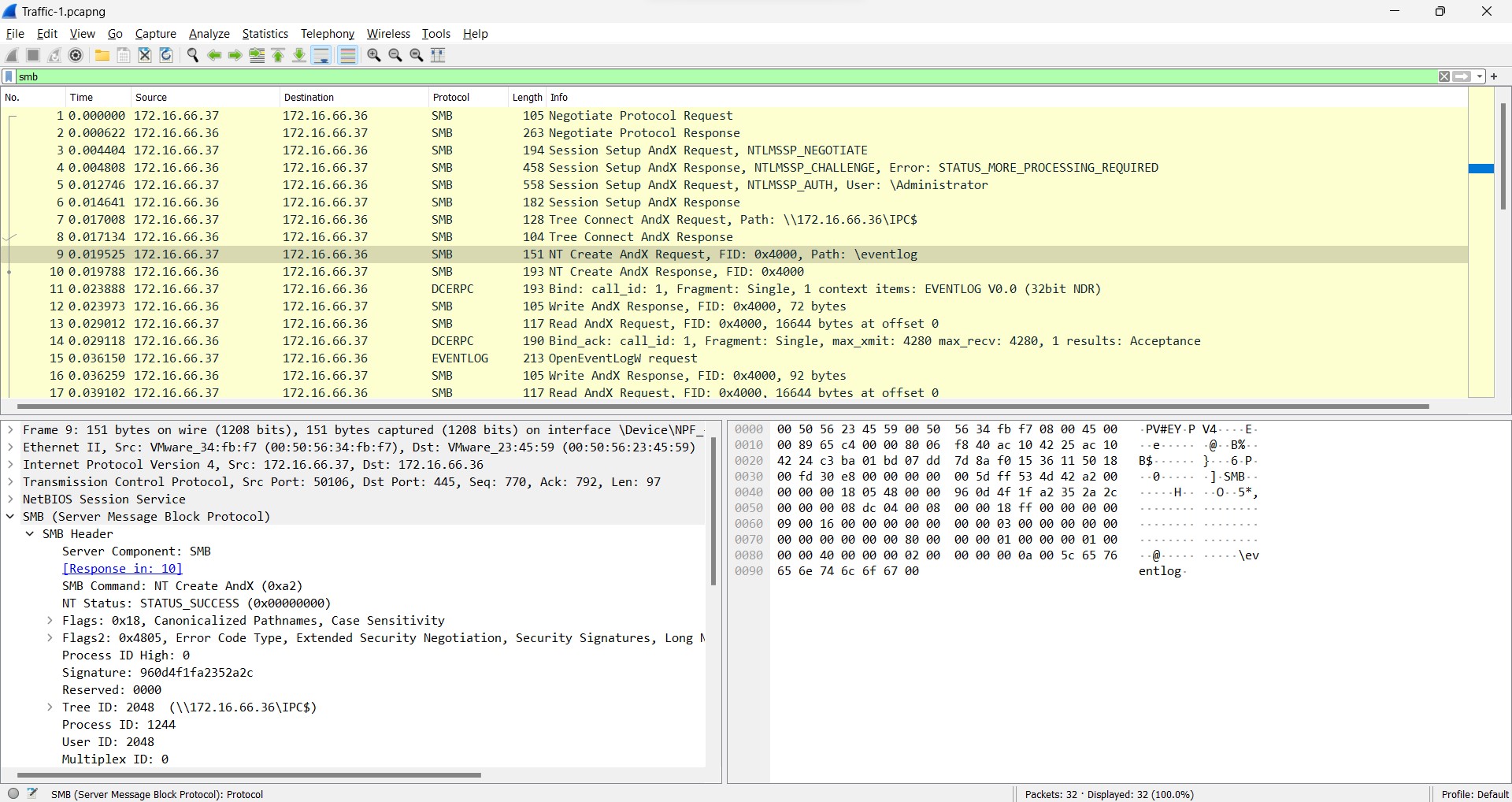
Q3) (File => Traffic-1) What is the name of the file that was opened?
On the same with previous filtering string, if we carefully look through each packet, you would see that the user have opened a file rightaway.
Answer: ev******
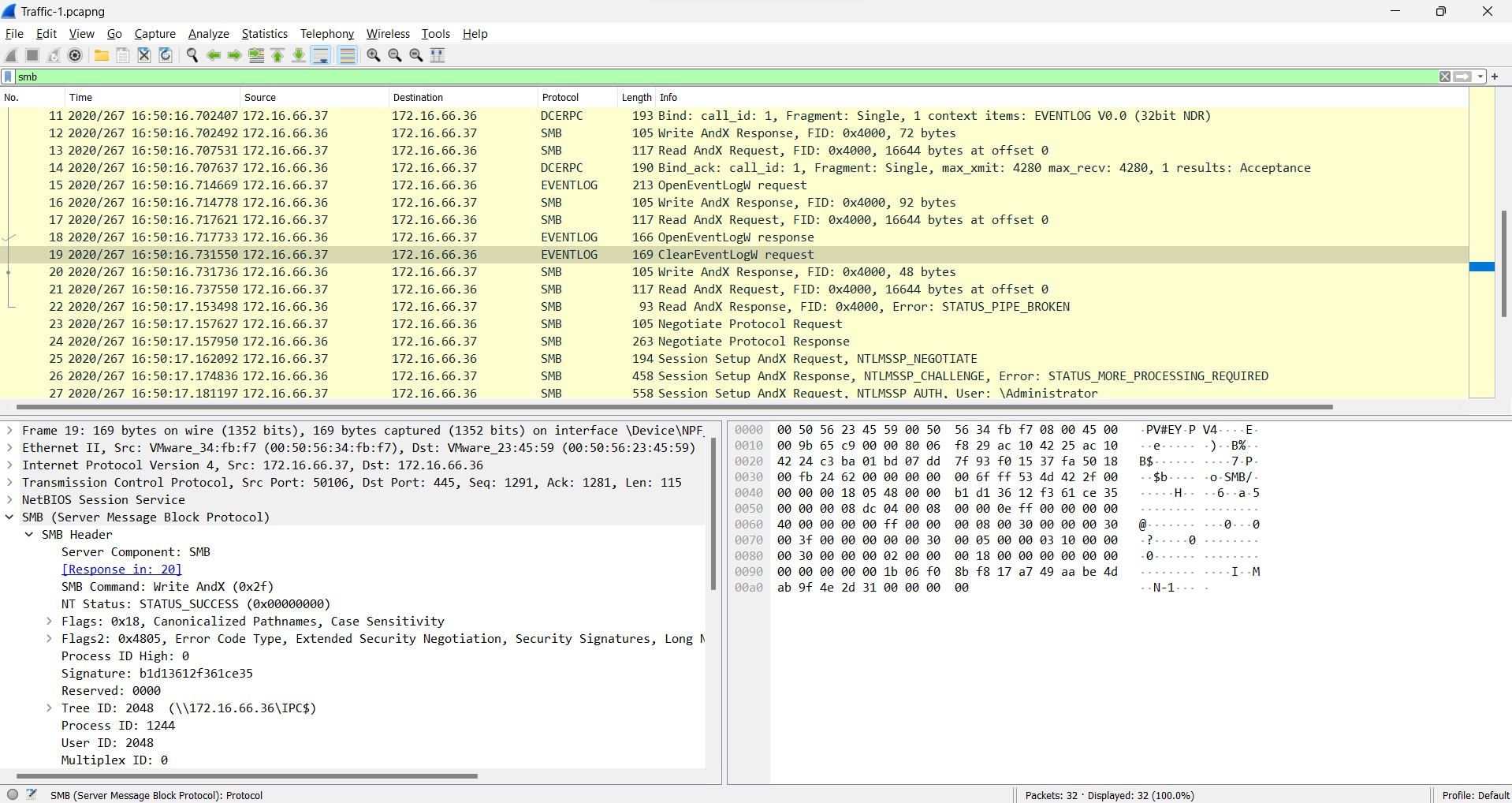
Q4) (File => Traffic-1) What is the timestamp of the attempt to clear the event log? (24H-UTC)
By default, wireshark uses the time format which counts in a second since the packet first captured. Therefore, we have to change the time format first to achieve what we are looking for.
To do this, we can go to View > Time Display Format and then choose for UTC time format.
By following the packet info, there is one packet info tells us about clearing eventlog and we just look at the timestamp and submit the answer.
Answer: 2***-**-** **:**:1*
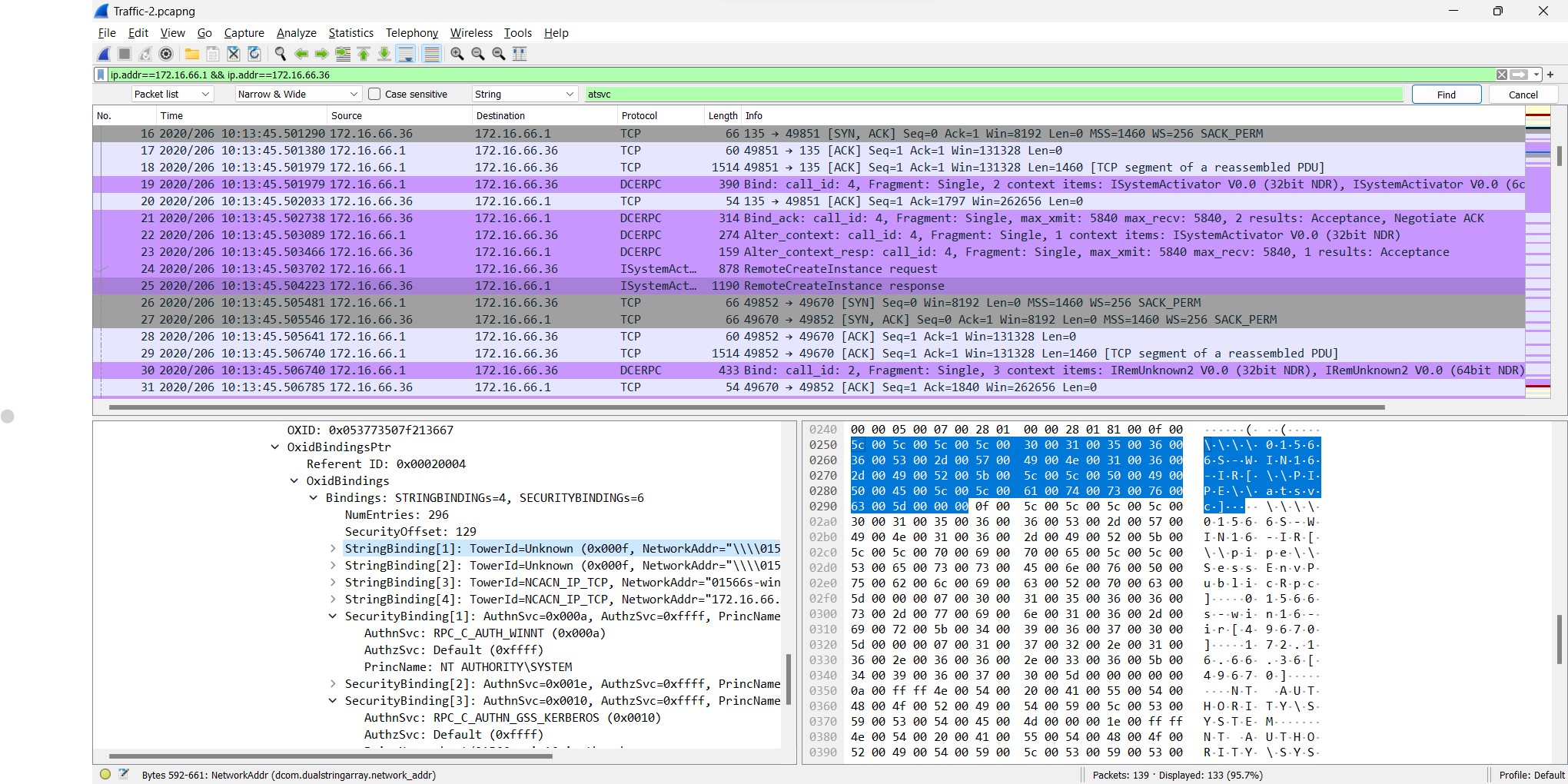
Q5) (File => Traffic-2) An attacker used a named pipe for communication to blend in and evade detection. What is the name of the service that utilized this pipe for communication?
The question takes me a few moment to understand the question, as well as a lot of time to take a look at the packet as well. By looking at the DCERPC protocol, I was hit by one interested protocol called “ISystemActivator” where it tells us a crucial message Remote Create Intance and it spots me to investigate it.
By looking at the response, we would see the answer rightaway, but keep looking carefully.
Answer: at***
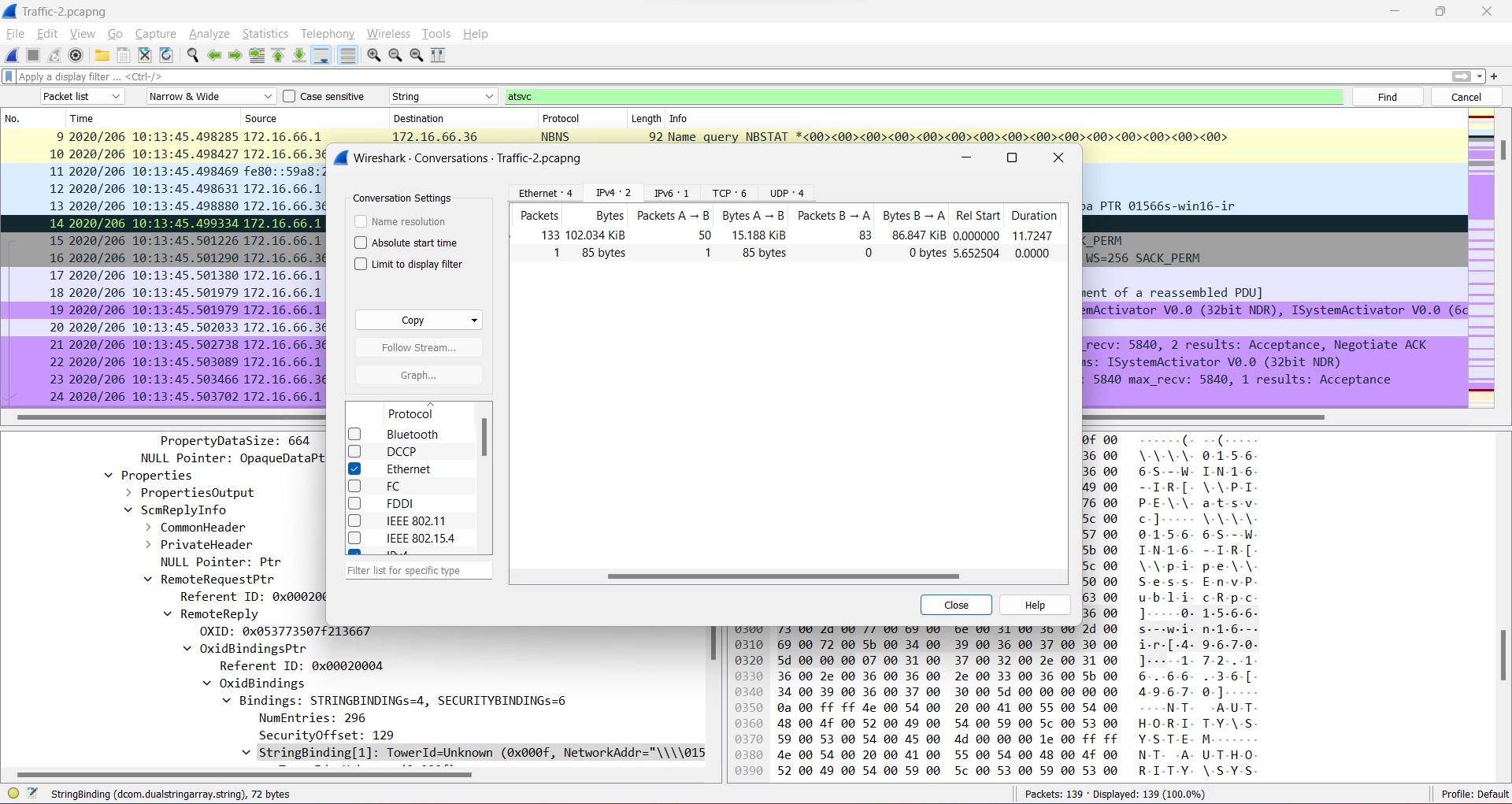
Q6) (File => Traffic-2) What was the duration of communication between 172.16.66.1 and 172.16.66.36?
By navigating to Statistics > Conversations, on the TCP tap, you would see the information which describes the duration of communicating between thos IPs.
Answer: 1*.****
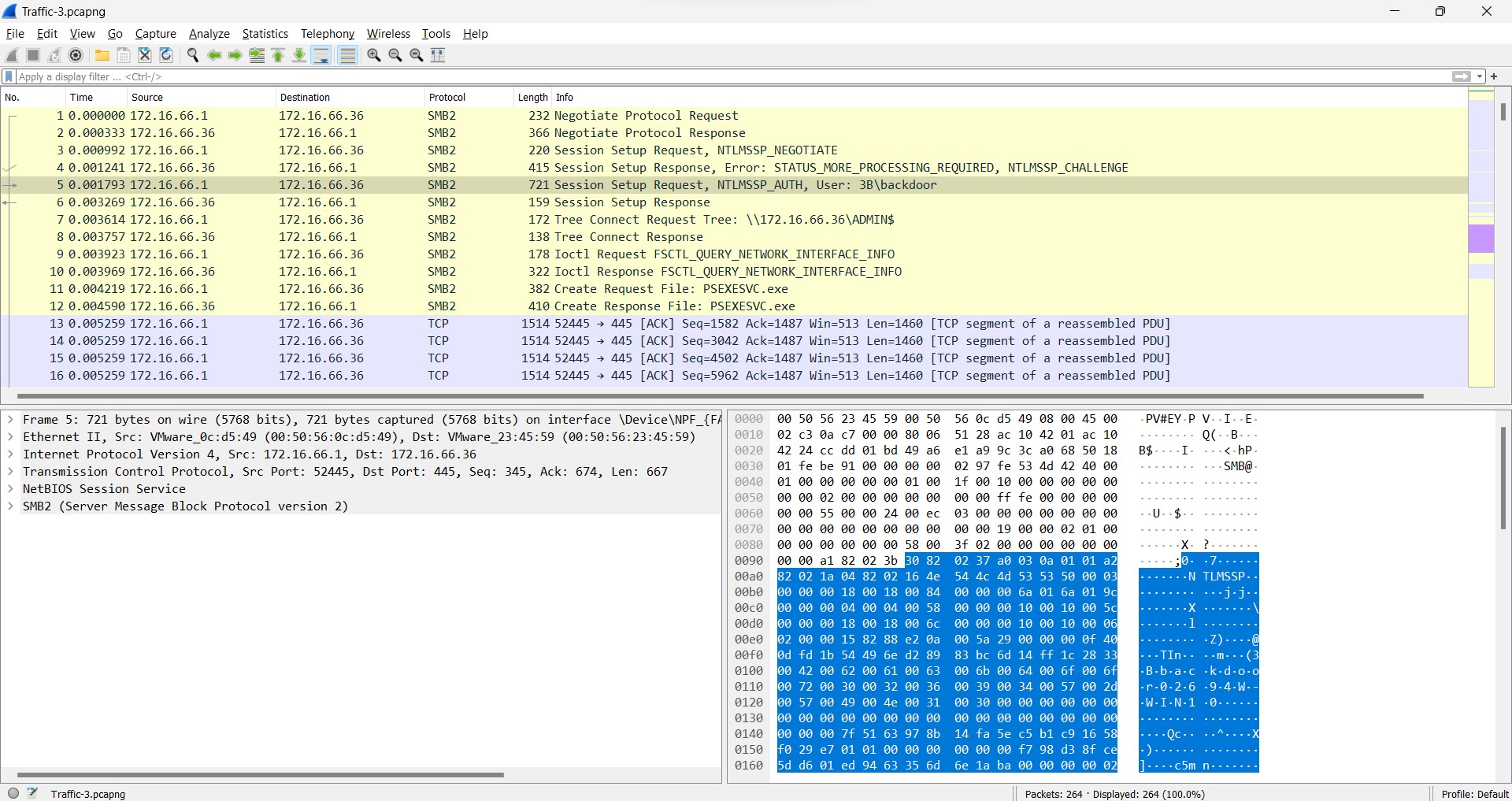
Q7) (File => Traffic-3) Which username is used to set up requests that may be considered suspicious?
On the third pcap, by looking through the packet info, there is a suspicious session setup requested to set up an username which I definitely sure that it was performed by malicious actor.
A username requested to be set up is obviously telling its purposes. Therefore, the answer is …
In real case, the malicious actor might use more tricky which would let investigator potentially overlook. To defense against this, it would be great if we record all legit users within each system on the documents.
Answer: b*******
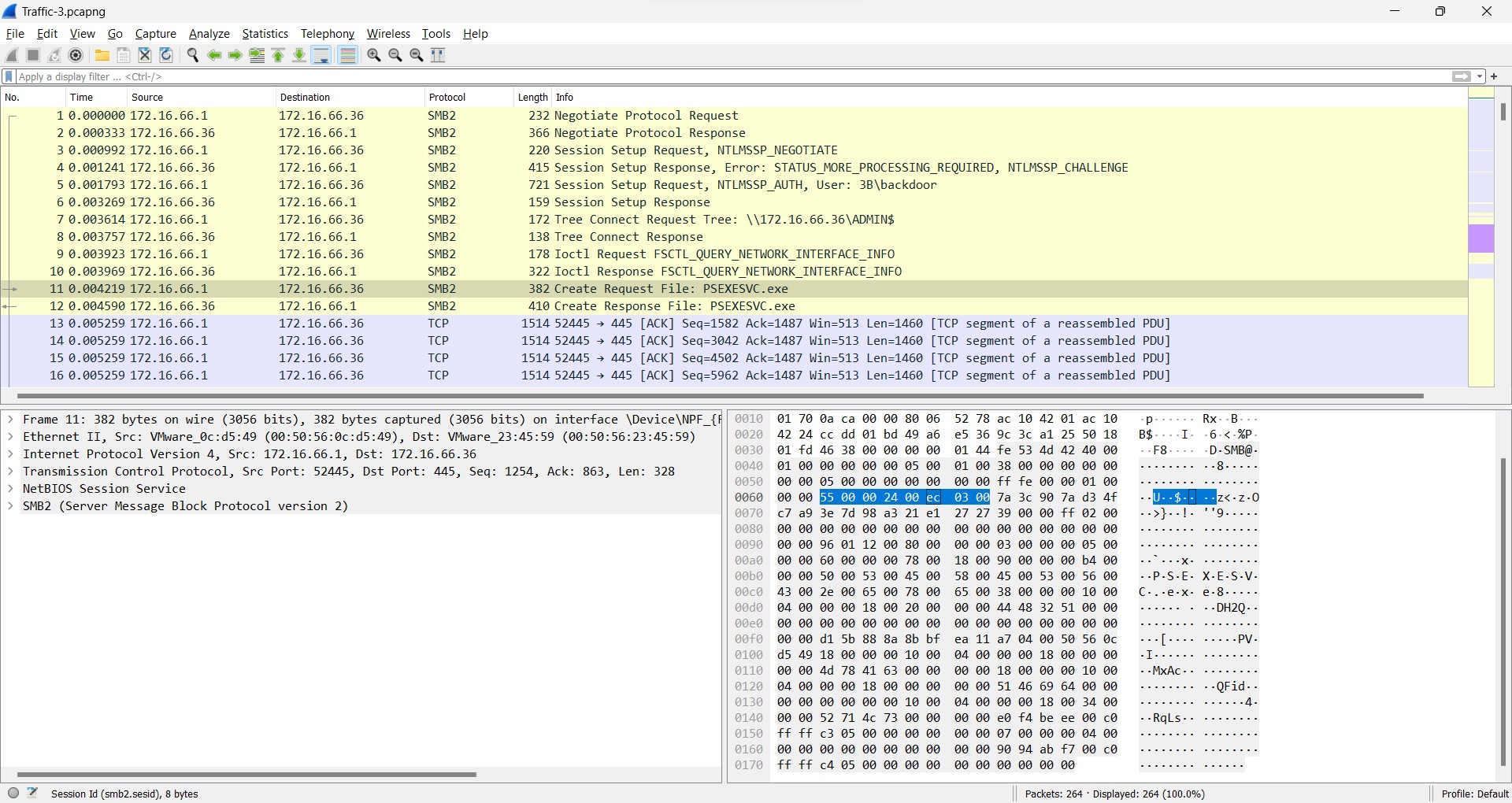
Q8) (File => Traffic-3) What is the name of the executable file utilized to execute processes remotely?
If you are familiar with the Windows remote execution utility, you would get the answer immediately, except you are not looking at the packet yet.
Answer: P*******.exe