Information
Category: Digital Forensics
Level: Medium
Scenario: John Doe was accused of doing illegal activities. A disk image of his laptop was taken. Your task as a soc analyst is to analyze the image and understand what happened under the hood.
Supportive Tools
- FTK Imager
- Autopsy
- rifiuti2
- [Browsing History View(https://www.foxtonforensics.com/browser-history-viewer/)]
- WinPrefetchView
- ShellBagsExplorer
- mimikatz
- Metdata Extractor
- Online Hash Crack
- NTLM Hash
Walkthrough
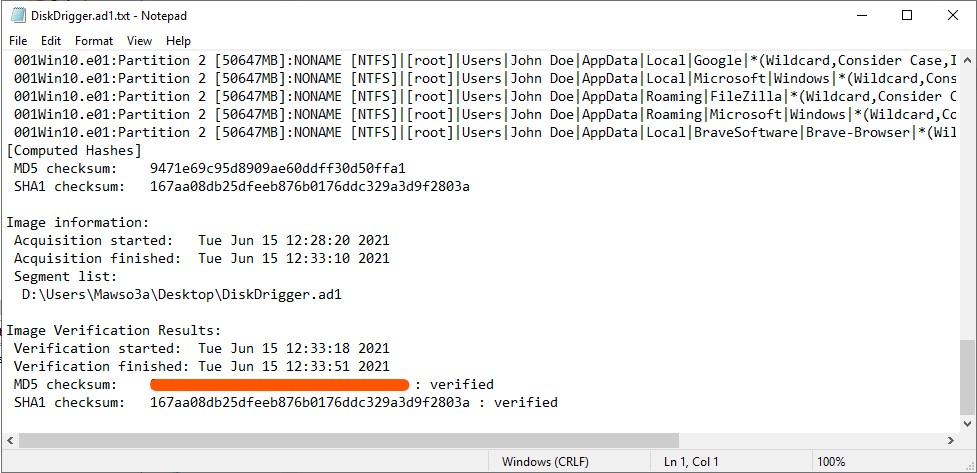
Q1) What is the MD5 hash value of the suspect disk?
Thanks, FTKImager for quickly identify this for us. There are several methods to get the MD5 hash of the suspected hard drive image. However, the most quickest way is to look at FTKImager generated metadata file which would be generated after we successfully acquired the evidence for verification purposes. In this case, DiskDrigger.ad1.txt and the answer would appear straightaway.
Note: Another way to get verification hash of suspected image is to use command such as,
md5sum <disk-image>.ad1for linux, orcertutil -hashfile <diskimage>.ad1 md5for windows.
Answer: 94******************************
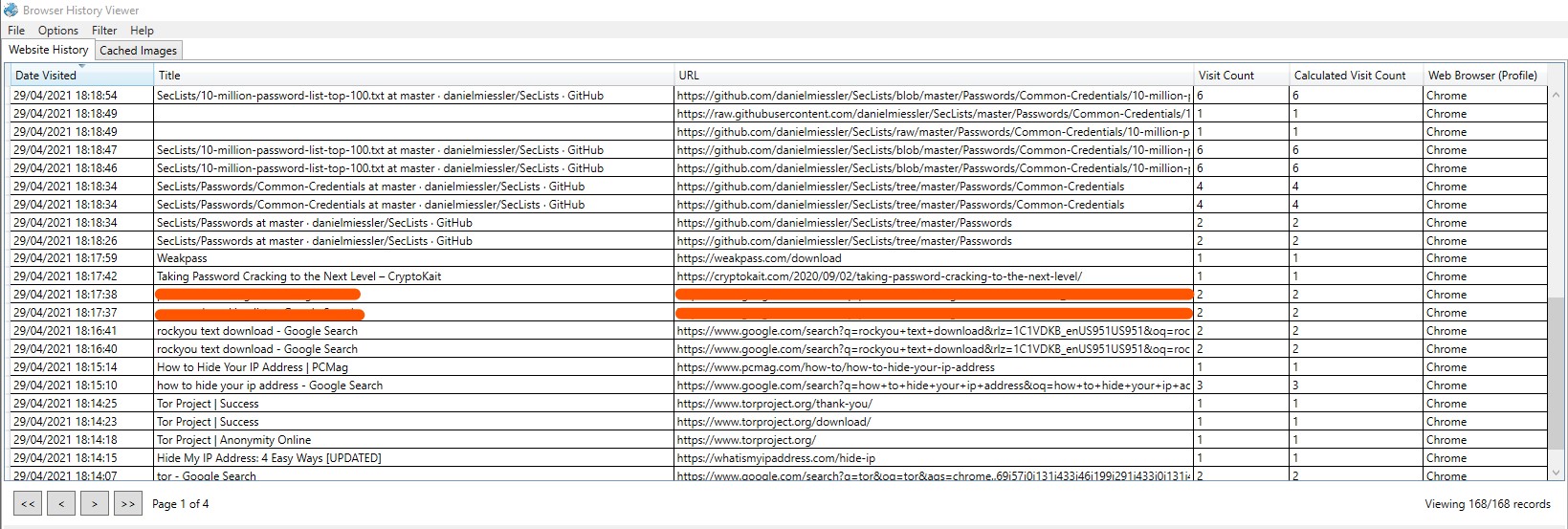
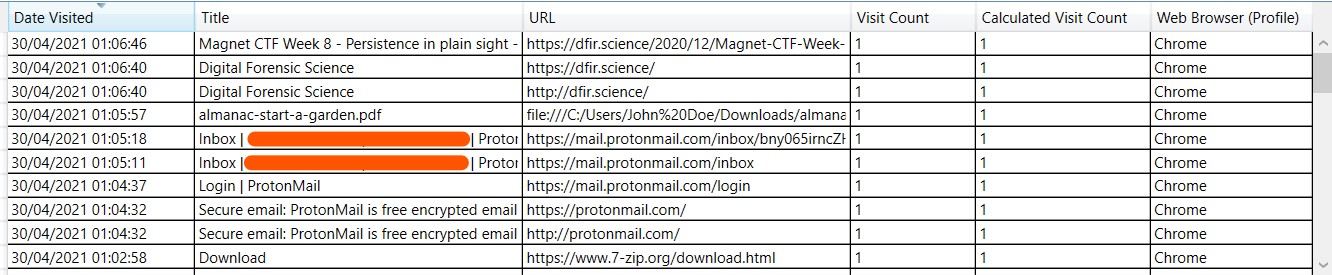
Q2) What phrase did the suspect search for on 2021-04-29 18:17:38 UTC? (three words, two spaces in between)
By looking at the C:\Users\John Doe\AppData\Local\Google\User Data\Default where the interested Google Chrome files are located in. There is a file named History which is SQLite3 format. In this case, if we use SQL Database Viewer it would make us spend a lot of time to identify and convert the time to UTC. Therefore, there is a tool named Browsing History Viewer which would give us much better viewer when we perform web browser forensics.
To achieve this, we must export or mount the image folder to our system. Followed by opening Browsing History Viewer and load the evidence history.
As shows on the picture above, during 2021-04-29 18:17:38 UTC the suspected had searched for something on Google Search Engine.
Answer: pas***** c******* l****
Q3) What is the IPv4 address of the FTP server the suspect connected to?
This take me a while to figure out where the FTP server file would be located. After do some quick research, the Suspected PC had installed FileZilla which uses to connect to the FTP remote server.
By looking at C:\Users\John Doe\AppData\Roaming\FileZilla\filezilla.xml, I saw an interested xml tag which describes the information about connected server including, host, port, protocol, type, and so on.
At this time, we are interested in Host and the answer is straightaway.
Answer: 1**.***.1.2*
Q4) What date and time was a password list deleted in UTC? (YYYY-MM-DD HH:MM:SS UTC)
In Windows OS GUI, deletion does not mean permanent delete, yet moving file to the Recycle Bin folder which is located in C:\$Recycle.Bin\ instead.
By default, the folder is maintained as a hidden file. Inside the root folder, there are several folders which is defined by User’s SID depending on the amount of your local user you have.
The Recycle bin artefacts that we are interested in is prepended with $I where we can find metadata, such as file deletion date, original filepath, file size, etc.
To find the answer, go to C:\$Recycle.Bin\<SID>\ where the SID is the John Doe’s SID. Then take a look on the modified date of the $I***** file so the answer is straightaway (Don’t forget to change timestamp to 24-hours format).
Note: Another way, I think is the best practice rather than I did on this question, is to use
$I Parserto parse the$I****file instead of just looking at the last modified date on FTK Imager.
Answer: YYYY-MM-DD 18:**:** UTC
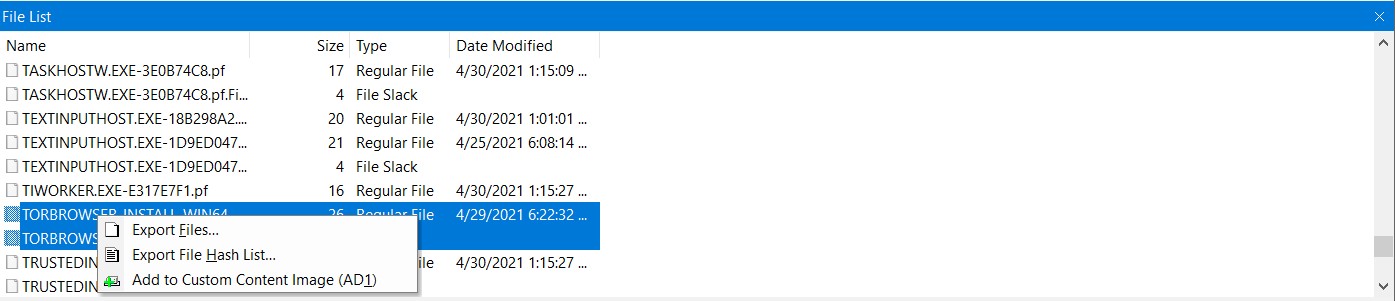
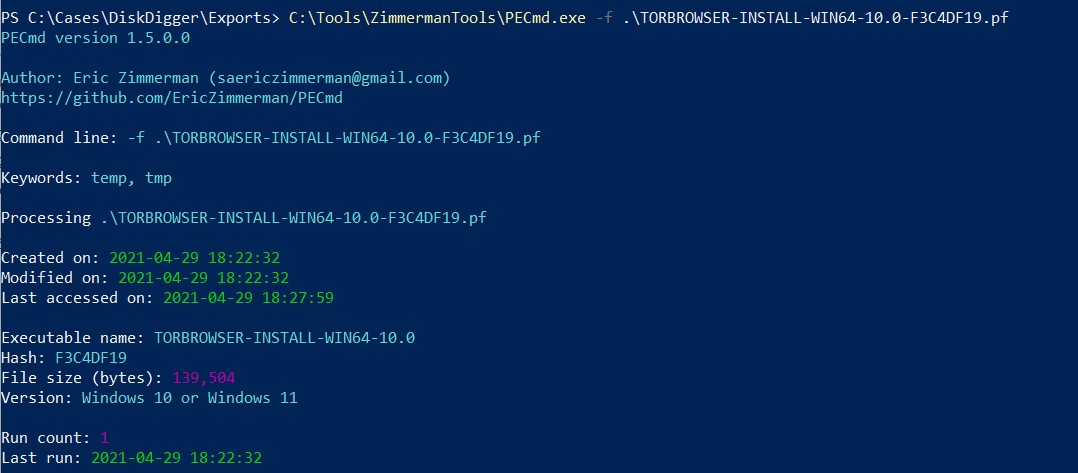
Q5) How many times was Tor Browser ran on the suspect’s computer? (number only)
To achieve this goal, we can quickly go to C:\Windows\Prefetch\ where it contains the files intended to speed up the the app’s load time whenever you run it. In this case, we are looking for Tor Browser’s prefetch file which we can found it in the prefetch folder.
Note: Windows would create a prefetch file every time you run an app for the first time.
By using PECmd.exe from Zimmermantools you can see the result show that the program hasn’t run yet. The prefetch we have seen previously was the installation process. However, to confirm the truth I used PECmd.exe to analyze the exported prefetch file to whether it is an installation prefetch or not.
Answer: 0
Q6) What is the suspect’s email address?
Follow the same process as demonstrated on Question 2, I have found interested user’s history where the suspected user had explored to the protonmail.
Answer: dr********[email protected]
Q7) What is the FQDN did the suspect port scan?
When we are talking about port scan, nmap would be the first choice in our mind. Therefore, I first go to investigate the Powershell Command Log which located in C:\Users\John Doe\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\. This file would give information about the past executed command through powershell.
As shows on picture above, the suspected user used the nmap to perform port scanning through powershell and we could see the answer rightaway.
Answer: df**.*******
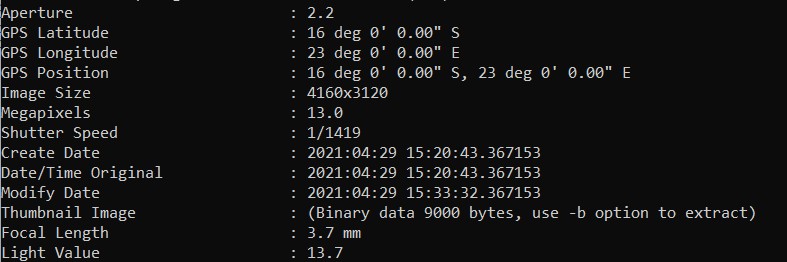
Q8) What country was picture “20210429_152043.jpg” allegedly taken in?
On the evidence drive, we go to C:\Users\John Doe\Pictures\Contact\ where the file “20210429_152043.jpg” is located. Then export the picture to your forensic workstation.
By using exiftool you could get metadata about the picture. Therefore, we could also retrieve the GPS location on the file as well. After getting the GPS location, just put the value on google maps and you would get the answer rightaway.
Answer: Z****
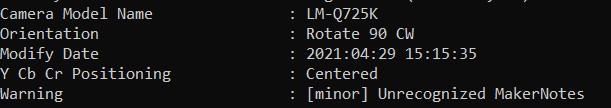
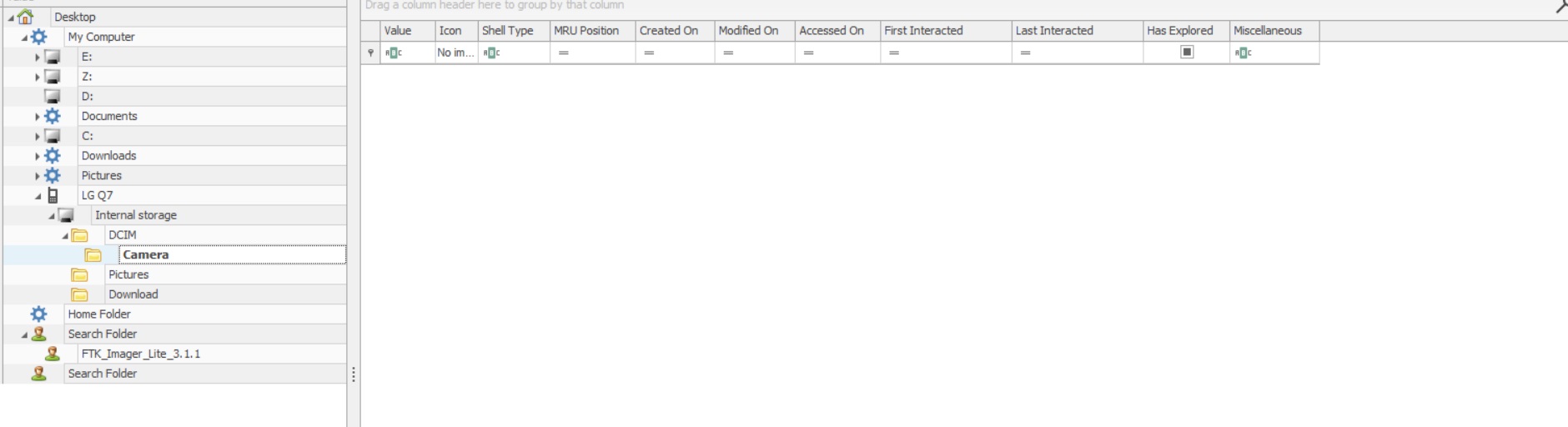
Q9) What is the parent folder name picture “20210429_151535.jpg” was in before the suspect copy it to “contact” folder on his desktop?
This question took me a while. First, I gathered information about the file by using exiftool and found that the phone model which uses to take this picture is LM-Q725K.
I performed a research and found that there are interested file about the user’s viewed folder called Shellbag.
To achieve the goal, we use ShellBagsExplorer from ZimmermanTools to read the file which is located in C:\Users\John Doe\AppData\Local\Microsoft\Windows\UsrClass.dat
Answer: C*****
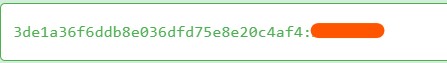
Q10) A Windows password hashes for an account are below. What is the user’s password? Anon:1001:aad3b435b51404eeaad3b435b51404ee:3DE1A36F6DDB8E036DFD75E8E20C4AF4:::
Go to Hashes.com and crack the the NTLM hash given by the challenge.
Answer: A*R**A*
Q11) What is the user “John Doe’s” Windows login password?
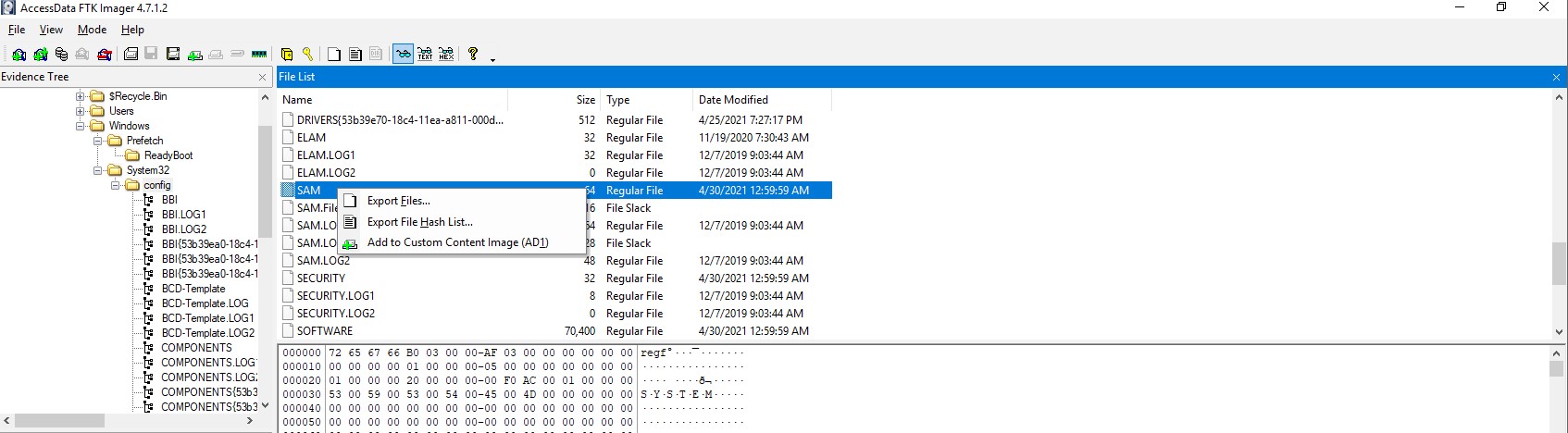
To achieve this, we have to export the windows registry file “SAM” and “SYSTEM” which are located in C:\Windows\System32\config\.
Then using mimikatz.exe to dump the users’ password hashes.
Finally, discover to Hashes.com and crack the the John Doe’s password.
Note: SAM, a.k.a. Security Accounts Manager is a database file in the Microsoft Windows operating system (OS) that contains usernames and passwords.
Answer: c*f***1