Introduction
Konnichiwa everyone! I hope you are doing well and thanks for reading my article. Today, as part of my study for certification exam. I’ve built my own lab using Splunk and wrote a short blog on how I setup it.1 Where I think it’s very crucial rather than just completing the course material provided by the certification provider.
Along with practicing on SIEM, I also learn to use tools for network monitoring and investigating such as, Suricata, Wireshark, and etc. By using these tools, It can support me on analyzing network traffic to hunt for any suspicious activities that may caused the system breach. For example, we can use Wireshark to see the captured packets and hunt for abnormaly activities behind the normal traffic. However, I’m not an experienced analyst who is advanced in network analysis. I also find somehow to help me on detection. Luckily, we have an open-source IDS/IPS like Suricata which can help us to detect the abnormal packets.
Suricata2 is a powerful rule-based IDS/IPS for network traffic monitoring and detection for any potentially threats. Therefore, I decided to use this tool as part of network traffic analysis. One thing I loved about the Suricata is we can monitor in real-time or captured file as well. Furthermore, we can use it with tcpreplay to replay captured network traffic for testing the effectiveness of security systems and applications.
When we talk about simulating or replaying the captured network traffic, the network we replayed will use the live network interface to replay those packets which would be disrupting live traffic and causing the network connectivity issues or unexpectedly behavior for applications using that network connection.
So, there are an interface called “dummy” that can aid this issue. In this article would take you through what is it? Why do we need it? and How to set up it?
TLDR; let’s get start!
What is dummy interface?
Dummy interface is a virtual network interface created within software and doesn’t represent a physical interface.
It serves various purposes, including simulating network environments for testing, facilitating advanced routing within a single machine, and providing isolation for specific use cases.
Why do we need it?
Using a dummy interface during network traffic replay with tools like tcpreplay is crucial to avoid unintended consequences on live networks and enhance security by isolating the replayed traffic.
In the cybersecurity, we can use dummy interface to replay network traffic that contained malicious activities to test our written rule if it can detect those attacks before applying to the production environment.
How to config dummy interface on your Linux box?
- Dummy interface requires having a dummy module loaded. There are two ways to achieve this goal where the first method is the permanent way which you can appending to the
/etc/modules. On the other hand, we can just temporarily loading this module by using command below:
1
secadmin@kali:~# modprobe dummpy
- Next step, we can create an interface by performing as depicting below,
1
2
3
secadmin@kali:~# ip link add <dummy_int_name> type dummy
secadmin@kali:~# ip addr add 10.10.30.1/24 dev <dummy_int_name>
secadmin@kali:~# ip link set <dummy_int_name> up
Optional:
Another way we can perform is to create a dummy interface using configuration file. We can achieve this by creating a file like
ifcfg-<dummy_int_name>within the/etc/network/interfaces.d/directory. Within the the file we can write a configuration as shows below,
- Checking whether it is done as we expected or not
1
secadmin@kali:~# ip -br addr show
- To set the dummy interface as promiscuous mode
1
secadmin@kali:~# ip link set <dummy_int_name> promisc on
- Again, to verfiy if the dummy interface is working as promiscuous mode we can perform as shows below,
1
secadmin@kali:~# ip addr show <dummy_int_name> | grep -i promisc
Using Dummy Interface with Suricata
As part of my testing here, I used the PCAP file from malware-traffic-analysis.net3 which I will use Suricata to detect icedID infection4.
- First, setting up the suricata using scripts below,
1
2
3
4
5
6
7
8
9
10
11
12
13
#!/usr/bin/env bash
if [[ $(id -u) -eq 0]]; then
# Add the Suricata package
apt-get install software-properties-common && add-apt-repository ppa:oisf/suricata-stable
apt-get update
# Install the latest stable version of Suricata
apt-get install -y suricata
# Update Suricata Rules
suricata-update
else
echo "Please running as root"
fi
- Then you can download the and extract the sample captured traffic as shows below,
1
2
3
4
wget https://malware-traffic-analysis.net/2021/02/22/2021-02-22-IcedID-infection-traffic.pcap.zip
# Extract the file with password "infected"
unzip 2021-02-22-IcedID-infection-traffic.pcap.zip
- Afterward, let’s run the suricata to live monitor the dummy interface
1
sudo suricata -i dummy0 -c /etc/suricata/suricata.yaml -l /var/log/suricata/
- Run another terminal windows and execute command below,
1
tcpreplay -i dumy0 -x 12 2021-02-22-IcedID-infection-traffic.pcap
- After spent a while, you can check the the
fast.logif there is any alerts triggered. If you follow the step aforementioned. The result might look something similar to mine.
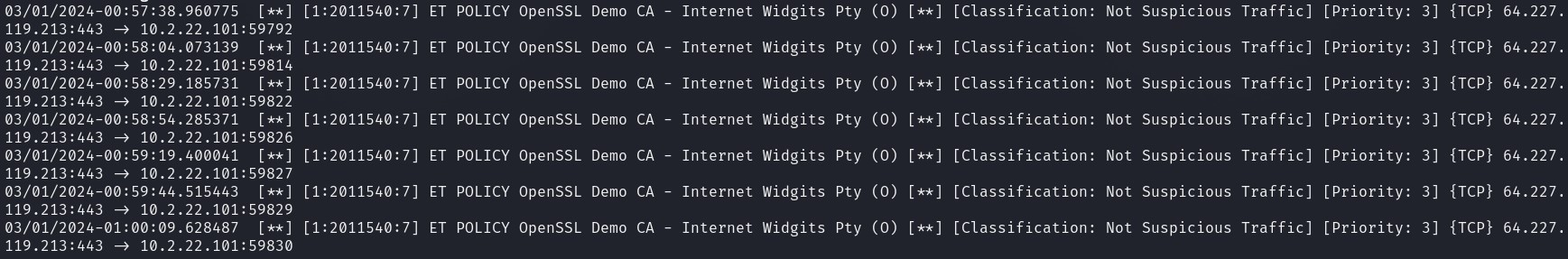 Figure 1-1 Suricata Alert Trigger Sample
Figure 1-1 Suricata Alert Trigger Sample
Note: I have terminated the tcpreplay process, so the alert is not completely covered all and your fast.log file may contain more alert than mine.
References
-
(2024, edscybersec), https://edscybersec.com/posts/installing-splunk-botsv2-dataset/ ↩
-
(2024, Suricata), https://suricata.io/ ↩
-
(2024, Malware Traffic Analysis), https://malware-traffic-analysis.net/ ↩
-
(2021, IcedID Infection PCAP), https://malware-traffic-analysis.net/2021/02/22/index.html ↩
