Introduction
Wireshark is a powerful and free-to-use network analysis tool that has been using widely from both network analysis and security professional all around the world which helps you capturing and analyzing network traffic. Therefore, knowing the feature of this tool is highly recommended to improve your traffic analysis.
However, the feature is not the only thing you need to improve to have a better network analysis skills.
“Knowing how to use Wireshark features to enhance network traffic analysis differs from having the skills to analyze network traffic.” — Security Blue Team
I’m totally agree with the statement mentioned above which is mentioning within the course. Wireshark is a tool and feature is such a thing facilitates us during the analysis. The deep understanding of what you are analysis, practicing, and experience are keys to success on this journey.
TL;DR, during this write up I would try my best to explain my mindset to the question and step I performed to solve the challenge which is a part of activity during the Introduction to Network Analysis course provided by Security Blue Team.
At the end of introduction, I highly recommend you to check out this free course. I found it really helpful and informative to those who want to jump into the field of Cybersecurity, especially who want to become blue teamer. Moreover, this would also help you to get familiar with SBT platform, if you are considering to purchase for BTL certification exam bundle.
Walkthrough
PCAP 1 Challenge
Which protocol was used over port 3942?
At the initial of my packet analysis methodology, what I always do is looking at the overall of the captured file. Therefore, I would directly to see Protocol Hierarchy to get insight of packets what were captured. This would help me to understand and predict the potentially surface that suspicious activities might be conducted.
We can perform this by going to Statistics > Protocol Hierarchy on Windows Bar, by doing so, the result would be as shown below.
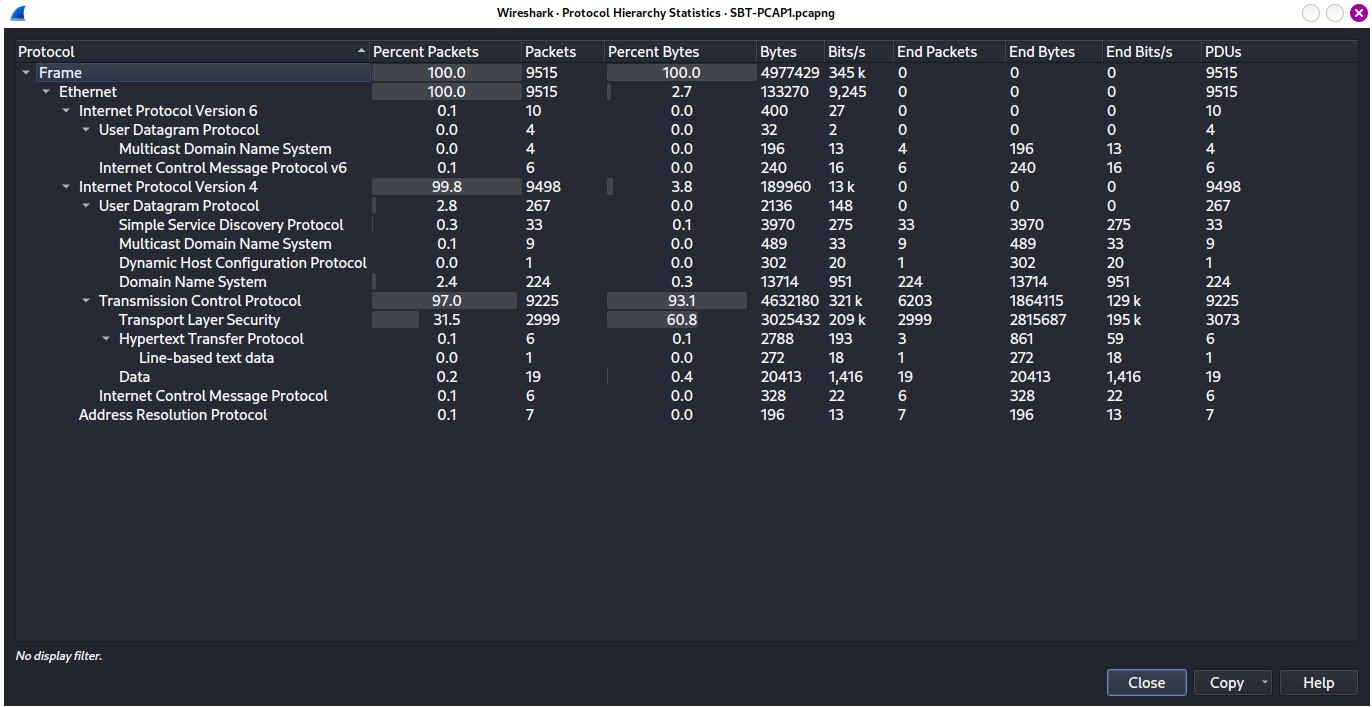 Figure 1.1 — Protocol Hierarchy of SBT_PCAP1.pcap file
Figure 1.1 — Protocol Hierarchy of SBT_PCAP1.pcap file
As Figure 1.1 depict, these captured file contains mostly of packet using TCP protocol (conduct reliable transmission) approximately 97%, where the 2.8% goes to UDP (unreliable, but provide with fast transmission) protocol.
After I get a broad picture of the capture file. Next, Following the question to find the protocol used by port 3942. But, how do we find that?
Well, within the course described us the way we can do to get briefly information about the host. To do so, navigating to Statistics > Endpoints which would summarize all hosts that were captured within this pcap. On the Endpoints windows, there are five main tabs appear including, Ethernet, IPv4, IPv6, and so forth, as show below.
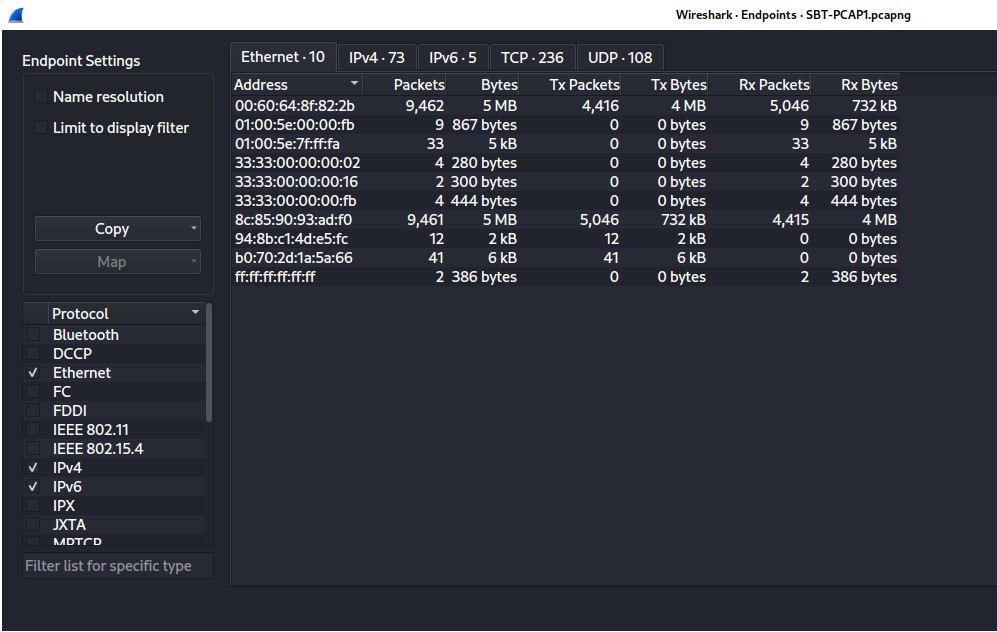 Figure 1.2 — Endpoints Windows of SBT_PCAP1.pcap file
Figure 1.2 — Endpoints Windows of SBT_PCAP1.pcap file
As picture depict, most traffic activity conducted using TCP protocol, where UDP is less than. However, my methodology is to look at the less packet that occurs within the network first, since it may the intention of threat actor to hide their activities from analyst like us.
Bingo! We found that port. To get insight of the packet we can click on that endpoint and then, right-click > Apply as Filter > Selected to filter the specific host used port 3942. On the packet list, you would see some packets related to our applied display filter as shown below.
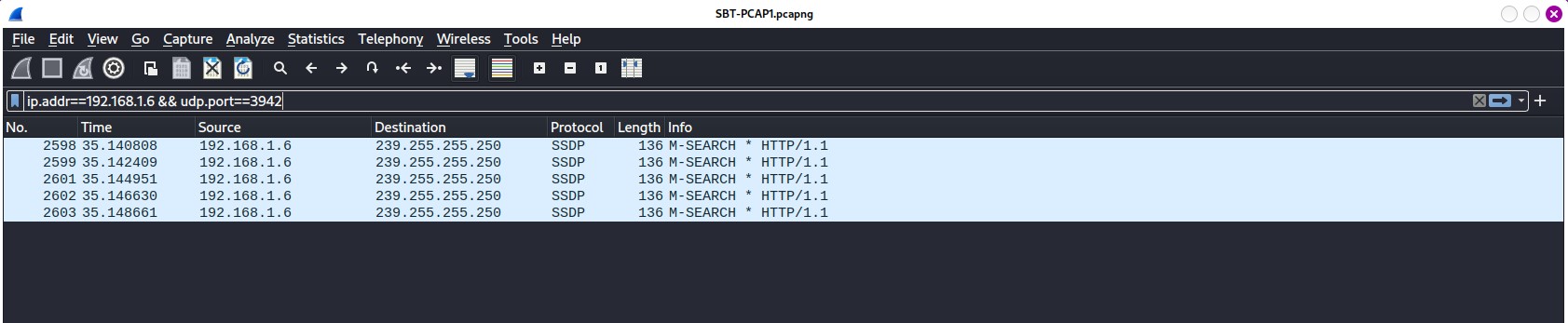 Figure 1.3 — Filtered result on port 3942 of SBT_PCAP1.pcap file
Figure 1.3 — Filtered result on port 3942 of SBT_PCAP1.pcap file
Hmm… pretty straightaway! I think the answer is there ;)
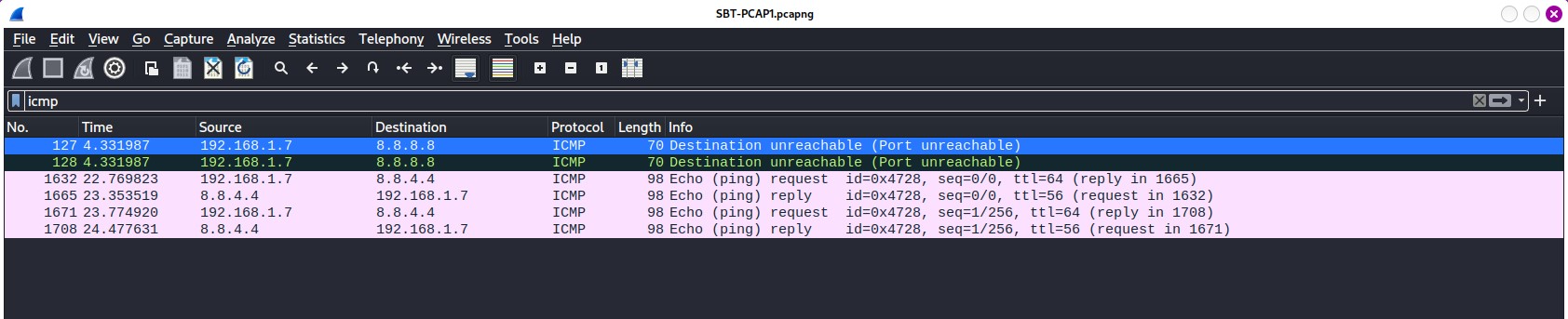
What is the IP address of the host that was pinged twice?
According to the last observation we did from the first question, now we are quite familiar with this packet capture. If you are looking at the protocol hierarchy thoroughly, you may see the Internet Control Message Protocol (ICMP) which is normally used to check the availability of the destination endpoint1.
To save our times, I use icmp to filter only ICMP packets. So, if you perform correctly the result would be as shown on below.
Since English is not my native language, I get confused at first which should be the answer between the host that perform ICMP request or the host the perform ICMP response? So, I decided to trust my gut. In my idea, I think the author means to find the host that pings back (response). Therefore, I come up with answering the Source address of the reply packet and It’s correct!
How many DNS query response packets were captured?
To break over this question, first, we need to filter out the noise. To do so, we can use dns.flags.response == 1 to get only packet that matches the dns response flag. The result would be as shown below.
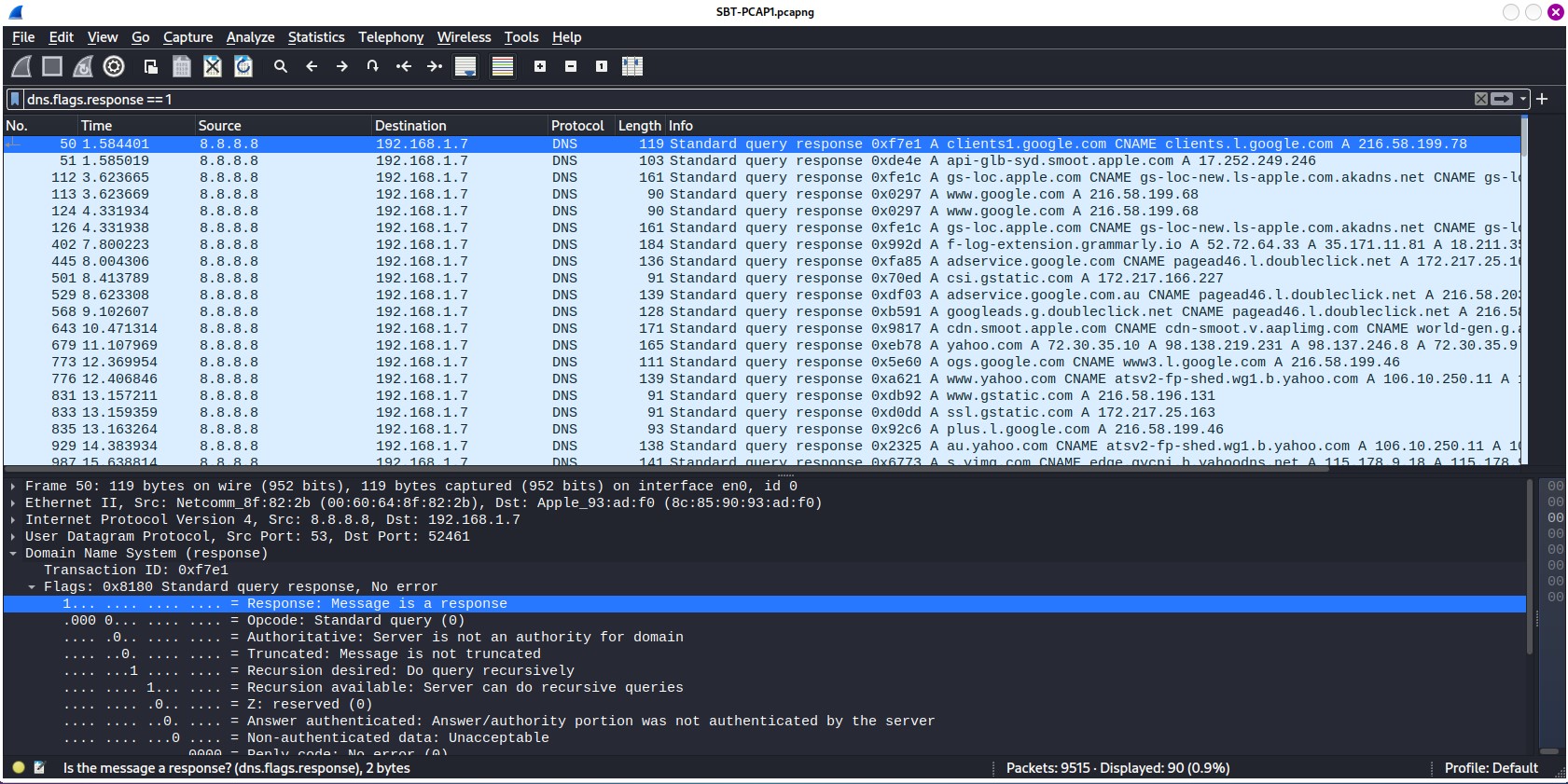 Figure 3.1 — DNS response filtered of SBT_PCAP1.pcap file
Figure 3.1 — DNS response filtered of SBT_PCAP1.pcap file
As Figure 3.1 depicts, you can see the Displayed message on the right bottom corner. The answer would be straightaways.
What is the IP address of the host which sent the most number of bytes?
Remember the feature of Wireshark we used ealier, Endpoints, we can find the most number of bytes their by going to Statistics > Endpoints and navigating to check all the tab to make sure that the IP address that produces the most number of bytes. At the end, I come up with the address of 115.178.9.18.
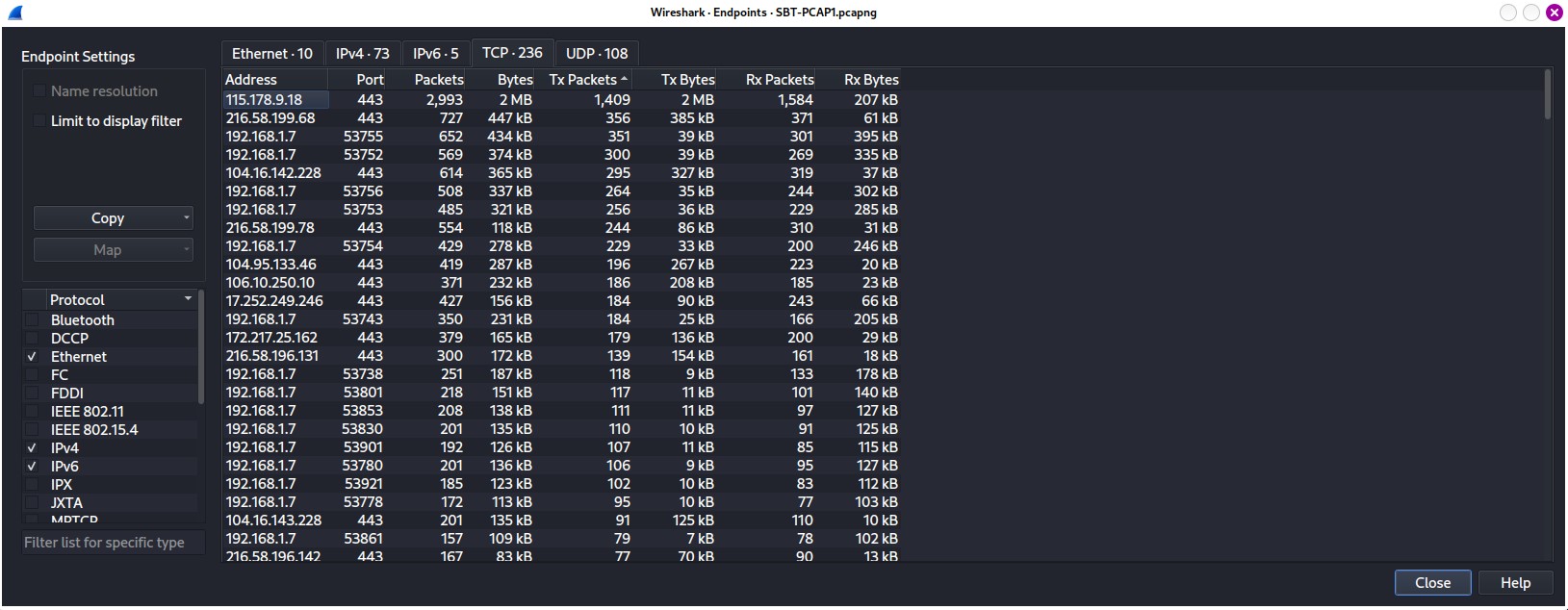 Figure 4.1 — Endpoints Windows Result filtered by the most number of bytes of SBT_PCAP1.pcap file
Figure 4.1 — Endpoints Windows Result filtered by the most number of bytes of SBT_PCAP1.pcap file
Conclusion
During my practice on the first challenge, I noticed that the questions and answers were relatively straightforward. This task, in what I believe is the author’s purpose, is to challenge you to enhance your analyzing skills while also growing your familiarity with Wireshark, which you must have as a starting point for the security analyst or network analyst role.
References
-
(Cloudflare, 2023), https://www.cloudflare.com/learning/ddos/glossary/internet-control-message-protocol-icmp/ ↩